The rise of the internet has brought about a whole new era of convenience and connectivity, allowing businesses and individuals to communicate, collaborate and engage with each other across the world. However, with the increasing dependence on these digital platforms comes a growing risk of cyber attacks. Among the most dangerous forms of cyber attacks is the Distributed Denial of Service (DDoS) attack, a type of attack that can cripple websites, online services and networks.
DDoS attacks involve flooding a website or online service with a massive amount of traffic, overwhelming the server and causing it to crash. The aim of these attacks is to disrupt the normal functioning of a website, making it inaccessible to users and causing significant financial losses for businesses. DDoS attacks are particularly harmful to e-commerce businesses, where website downtime can translate into lost sales and a damaged reputation.
Despite the severity of the threat posed by DDoS attacks, many businesses remain unprepared for these attacks. In some cases, businesses may not even be aware that they are being targeted by a DDoS attack until it’s too late. To effectively defend against DDoS attacks, it is essential to understand how they work, the various types of attacks and the tools and techniques used by attackers.
In this article, we will provide a comprehensive guide to DDoS attacks, from how they work to the various methods used to launch them. We will explore the different types of DDoS attacks, including volumetric attacks, protocol attacks, and application layer attacks, and discuss the tools and techniques used to launch these attacks. We will also delve into the various defenses against DDoS attacks, such as mitigation services, firewalls, and intrusion detection and prevention systems.
Moreover, we will discuss the importance of having a comprehensive incident response plan in place to minimize the impact of any attacks that do occur. This includes outlining the roles and responsibilities of team members, establishing communication protocols and backup plans, and conducting regular drills to test the effectiveness of the plan.
By the end of this article, readers will have a better understanding of the threat posed by DDoS attacks and the steps businesses can take to protect themselves against these attacks. We hope that this article will serve as a useful resource for businesses of all sizes, helping them to defend against the ever-evolving threat of DDoS attacks and maintain the availability and integrity of their online presence.
Points to Cover
- What does DDoS stand for?
- What is a distributed denial-of-service (DDOS) attack?
- Is Dos and DDoS same?
- Measuring the strength of a DDoS
- Why would anybody do this?
- What are commonly used DoS/DDoS attack tools?
- Types of DDoS Attacks
- How to identify a DDoS attack?
- How To Launch A DDoS Attack On A Specified Website
- How to DDoS an IP using cmd
- How can I defend against DoS/DDoS tools?
- FAQ
- Conclusion
What does DDoS stand for?
A DDoS attack is short for “Distributed Denial of Service”, and is the bigger brother of simpler denial-of-service attacks.
Imagine for a moment that you’re in a crowded coffee shop, trying to order your favorite latte. Suddenly, a group of rowdy customers swarms the counter, shouting and causing chaos. The overwhelmed baristas can’t keep up with the influx of orders, and the whole system grinds to a halt.
Now, imagine this same scenario playing out on a much larger scale, but in the digital realm. A DDoS attack is like a massive crowd of computers all trying to access a particular website or server at the same time, overwhelming the system and causing it to crash.
The “distributed” part of the name refers to the fact that the attack is usually orchestrated from a network of compromised computers, called a botnet. These computers have been infected with malware that allows the attacker to control them remotely, using them to flood the targeted system with requests.
In short, DDoS attacks are a digital form of chaos, designed to disrupt and overwhelm computer systems in a way that’s similar to a rowdy coffee shop crowd.
What is a distributed denial-of-service (DDOS) attack?
A distributed denial-of-service (DDoS) attack is like a digital stampede that can trample a website or online service into submission. It’s like a swarm of angry bees descending on a single target, overwhelming it with a barrage of traffic until it can no longer function.
Imagine you’re trying to open a door, but someone is pushing against it with all their might. No matter how hard you try, you can’t get the door to budge. That’s what a DDoS attack is like for a website or online service. The attacker uses a network of infected computers, known as a botnet, to send a flood of requests to the target, clogging its servers and rendering it inaccessible to legitimate users.
It’s not just about overwhelming the target, though. A skilled attacker can also use a DDoS attack as a smokescreen, distracting the target’s security team while they carry out other nefarious activities, like stealing data or planting malware.
DDoS attacks are a serious threat to the stability and security of the internet. They can disrupt critical services, cause financial losses, and even be used as a weapon in political or ideological conflicts. Defending against a DDoS attack requires a combination of technical expertise, infrastructure, and planning, as well as a deep understanding of the attacker’s motives and methods.
Is Dos and DDoS same?
While both are types of cyber attacks, denial-of-service (DoS) and distributed denial-of-service (DDoS) are like the difference between a single pebble and an avalanche.
Imagine you’re walking along a peaceful mountain trail, and suddenly someone throws a pebble at you. It stings a little, but you can brush it off and keep going. That’s what a DoS attack is like: a single computer bombarding a website or service with traffic in an attempt to overwhelm it.
Now imagine that same mountain, but this time it’s covered in snow. Suddenly, a massive avalanche comes hurtling down, burying everything in its path. That’s what a DDoS attack is like: a network of compromised computers, called a botnet, all targeting the same website or service with a flood of requests, overwhelming it and causing it to crash.
In a DoS attack, the attacker typically uses a single computer or internet connection to flood the target with traffic, while in a DDoS attack, the attacker uses a botnet to orchestrate a coordinated attack from multiple sources. DDoS attacks are more complex, sophisticated, and difficult to defend against than DoS attacks.
Both types of attacks can have serious consequences, ranging from financial losses to reputational damage to compromised data. Defending against these attacks requires a combination of technical expertise, infrastructure, and planning, as well as a deep understanding of the attacker’s motives and methods.
Measuring the strength of a DDoS
According to this study, 82% of attacks last less than 4 hours. In terms of bandwidth volume, 34% clock in at between 100 MB’s to 1 GB’s, and only 5.3% exceed the 10 GB/s mark.
A 1 GB/s denial-of-service attack is strong enough to take down most of the websites out there, since their data hosting simply doesn’t offer enough bandwidth to keep the site online.
One of the biggest ever recorded was the Mirai botnet attack in Autumn 2016, coming at over 1 terabytes per second. It overwhelmed the Dyn DNS provider, and then the effect cascaded, temporarily taking down major websites such as Reddit or Twitter.
Nowadays, even beginner hackers who can’t even code to save their life (called script kiddies) have access to big and powerful botnets-for-hire that can flood a target with 100 GB/s. This type threat isn’t going away, quite the contrary. Quite the contrary, it will only become powerful and widely accessible than before.
Why would anybody do this?
Compared to other kinds of cyber attacks, DDoS attacks are messy, overly destructive, and very difficult to pull off. Because of this, they don’t make much sense from a financial perspective.
So cybercriminals might use them as a blunt weapon against some of their competitors. For instance, they might want to bring down a site hosting a cybersecurity tool, or bring down a small online shop operating in the same niche.
In other cases, malicious hackers use them as a form of extortion, where the victim has to pay a fee in order for the denial of service to stop.
Also, a DDoS attack can act as a smokescreen, hiding the real endgame, such as infecting the target with malware or extracting sensitive data.
And in what constitutes a frequent scenario, the attacker might not even have a motive. Instead, he just does it for the “giggles”, seeking to test his abilities or just to cause mayhem.
What are commonly used DoS/DDoS attack tools?

Some commonly used tools include:
Low Orbit Ion Cannon (LOIC)
The LOIC is an open-source stress testing application. It allows for both TCP and UDP protocol layer attacks to be carried out using a user-friendly WYSIWYG interface. Due to the popularity of the original tool, derivatives have been created that allow attacks to be launched using a web browser.
High Orbit Ion Cannon (HOIC)
This attack tool was created to replace the LOIC by expanding its capabilities and adding customizations. Using the HTTP protocol, the HOIC is able to launch targeted attacks that are difficult to mitigate. The software is designed to have a minimum of 50 people working together in a coordinated attack effort.
Slowloris
Slowloris is an application designed to instigate a low and slow attack on a targeted server. It needs a relatively limited amount of resources in order to create a damaging effect.
R.U.D.Y (R-U-Dead-Yet)
R.U.D.Y. is another low and slow attack tool designed to allow the user to easily launch attacks using a simple point-and-click interface. By opening multiple HTTP POST requests and then keeping those connections open as long as possible, the attack aims to slowly overwhelm the targeted server.
Types of DDoS Attacks
There are several types of distributed denial-of-service (DDoS) attacks, each with its own unique characteristics and methods of operation. Here are some of the most common types:
- Volumetric Attacks: This type of attack floods the target with a massive volume of traffic, overwhelming its servers and making it inaccessible to legitimate users. Examples include UDP floods, ICMP floods, and SYN floods.
- Protocol Attacks: These attacks exploit weaknesses in network protocols, causing the target to consume excessive resources in trying to process the requests. Examples include Ping of Death, Smurf Attack, and Fragmentation Attack.
- Application Layer Attacks: These attacks target the application layer of the target, exploiting vulnerabilities in the software and overwhelming it with requests. Examples include HTTP floods, Slowloris, and HTTP POST floods.
- Distributed Reflection Denial of Service (DRDoS): This is a more advanced type of DDoS attack that uses a technique called IP address spoofing to amplify the attack, making it much more potent. The attacker sends requests to servers that are configured to respond with much larger data packets than the original request, amplifying the attack’s impact.
- IoT-Based DDoS Attacks: These attacks use compromised Internet of Things (IoT) devices, such as cameras or routers, to launch a coordinated attack. IoT devices are often easy to compromise, making them an attractive target for attackers.
DDoS attacks are a constantly evolving threat, and new types of attacks are emerging all the time. Defending against DDoS attacks requires a combination of technical expertise, infrastructure, and planning, as well as a deep understanding of the attacker’s motives and methods.
How to identify a DDoS attack?
The most obvious symptom of a DDoS attack is when a site or service suddenly starts behaving lethargic, becoming too slow or unavailable. There might be a possibility that the site may start reacting gradually. But such a legitimate spike in traffic — can create similar performance issues, so need to be investigated because any kind of such interruption, contingent upon your setup, can be crushing to your business.
The symptoms of DDoS assaults include:
- The site is reacting gradually
- The site is lethargic
- The client has issues getting to the site
There are other, more specific signs of DDoS attacks that can vary depending on the type of attack.
Online Traffic analytics tools can help you spot some of these DDoS attack indication signs of a DDoS, these tools can help you get aware of :
- Suspicious amounts of traffic originating from any single IP address
- Repeated traffic from users who share the same behavioral profile, such as device type, geolocation, or web browser version
- An unexplained surge in requests to a single page or endpoint
- Unnatural or Odd traffic patterns such as spikes at odd hours of the day (e.g. a spike every 20 minutes)
How To Launch A DDoS Attack On A Specified Website
To launch a successful distributed denial-of-service (DDoS) attack, it is important to have a basic understanding of how these attacks work. In essence, a DDoS attack floods a targeted website or server with an overwhelming amount of traffic, rendering it inaccessible to legitimate users.
There are various ways to execute a DDoS attack, including sending a large volume of data to the target website or using a botnet to generate multiple requests to the website. Attackers can employ an array of tools to launch these attacks, ranging from specialized DDoS attack software to custom-built DDoS attack scripts.
However, it is critical to note that launching a DDoS attack is illegal and unethical. These attacks can cause significant damage to businesses, organizations, and individuals, leading to financial losses, reputational damage, and compromised data. Furthermore, law enforcement agencies worldwide are increasingly cracking down on DDoS attackers, and those caught can face severe legal consequences.
Choose the Right DDoS Attack Tool
Choosing the right DDoS attack tool is a critical step in launching a successful DDoS attack, but it is important to remember that launching such an attack is illegal and unethical. That being said, understanding the differences between DDoS attack tools can help organizations better prepare for potential attacks and implement stronger cybersecurity measures.
There are various DDoS attack tools available, each with its own unique features and capabilities. Some of the most popular tools include LOIC, HOIC, and XOIC, which can be used to launch attacks such as TCP, UDP, and HTTP floods.
However, it is important to note that using DDoS attack tools is illegal and can lead to significant legal consequences. These attacks can cause serious harm to businesses and organizations, leading to significant financial losses and reputational damage.
Instead of relying on DDoS attack tools, organizations should focus on implementing robust cybersecurity measures to protect against potential attacks. This includes implementing firewalls, intrusion detection and prevention systems, and regularly testing for vulnerabilities.
Choose the Right Target Website
Choosing the right target website is a crucial step in launching a successful DDoS attack. However, it’s important to note that engaging in such attacks is illegal and unethical. Instead, organizations should focus on implementing robust cybersecurity measures to protect against potential attacks.
If one were to hypothetically engage in a DDoS attack, they would need to choose a website that is vulnerable to such attacks. Not all websites are created equal when it comes to DDoS vulnerability, so it’s essential to select a target carefully. For instance, smaller websites may be more vulnerable to attacks than larger ones, as they may have fewer resources to handle high volumes of traffic. Similarly, certain types of websites, such as those that provide essential services or online commerce, may be more vulnerable to DDoS attacks due to their critical nature.
It’s also essential to consider the size of the website when selecting a target. Larger websites may require more resources to launch a successful attack, so it’s important to factor this into the decision-making process.
It’s important to note that launching a DDoS attack is illegal and can lead to significant legal consequences. Instead of relying on these attacks, organizations should focus on implementing strong cybersecurity measures, such as firewalls, intrusion detection and prevention systems, and regular vulnerability assessments. In this way, they can better protect their websites from potential attacks and ensure the safety and security of their customers and users.
Launch the Attack
Once you have chosen the right target website and the right DDoS attack tool, you can begin to launch the attack. Depending on the type of attack you are launching, you may need to configure the attack tool to send the appropriate amount of traffic to the target website. Additionally, you may need to configure the attack tool to use the right type of attack, such as a SYN flood or a UDP flood. Once the attack is configured, you can launch the attack and monitor the results.
Monitor the Results
After launching a DDoS attack, it is crucial to monitor the results closely to ensure its success. Monitoring the target website is essential to verify that it is not responding to legitimate requests, and at the same time, monitor the attack tool to ensure that it is sending the appropriate amount of traffic.
It’s also vital to ensure that the attack tool is not sending malicious traffic to other websites. This could cause harm to innocent websites and networks, leading to significant legal consequences.
Protect Yourself from DDoS Attacks
Once you have launched the attack, it is important to protect yourself from any potential repercussions. You should ensure that you are using a secure connection when launching the attack, and you should also ensure that you are not using any personal information when launching the attack. Additionally, you should ensure that you are not using any malicious software when launching the attack, as this could lead to legal repercussions.
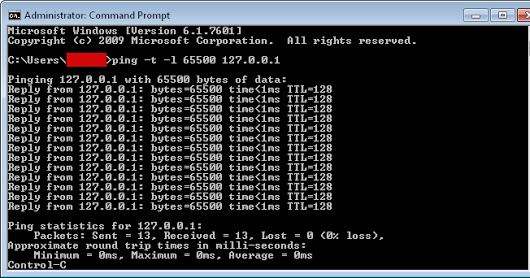
How to DDoS an IP using cmd
One of the most basic and rudimentary denial-of-service methods is called the “ping of death”, and uses the Command Prompt to flood an Internet Protocol address with data packets.
Because of its small scale and basic nature, ping of death attacks usually work best against smaller targets. For instance, the attacker can target:
a) A single computer. However, in order for this to be successful, the malicious hacker must first find out the IP address of the device.
b) A wireless router. Flooding the router with data packets will prevent it from sending out Internet traffic to all other devices connected to it. In effect, this cuts the Internet access of any device that used the router.
In order to launch a ping denial-of-service attack, the malicious hacker first needs to find out the IP of the victim’s computer or device. This is a relatively straightforward task, however.
A ping of death is small in scale, and fairly basic, so it’s mostly efficient against particular devices. However, if multiple computers come together, it’s possible for a handful of these to bring down a smallish website without the proper infrastructure to deal with this threat.
Using Google Spreadsheet to send countless requests
An attacker can use Google Spreadsheets to continuously ask the victim’s website to provide an image or PDF stored in the cache. Using a script, he will create a neverending loop, where the Google Spreadsheet constantly asks the website to fetch the image.
This huge amount of requests overwhelms the site and blocks it from sending outward traffic to visitors.
Unlike other denial-of-service tactics, this one doesn’t send large information packages to flood the website, but instead, it makes data requests, which are much, much smaller.
In other words, the attacker doesn’t need to rely on sizeable botnet or thousands of other users to achieve a similar effect.
Teardrop attacks
In most cases, the information transmitted between a client device and the server is too big to be sent in one piece. Because of this, the data is broken into smaller packets, and then reassembled again once it reaches the server.
The server knows the order of reassembly through a parameter called “offset”. Think of it as instructions to building a LEGO toy.
What a teardrop attack does, is to send data packets at the server that make no sense, and have overlapping or dysfunctional offset parameters. The server tries, and fails, to order the data according to the malicious offset parameters. This quickly consumes available resources until it grinds to a halt, taking down the website with it.
Amplifying a DDoS attack
To maximize every data byte, malicious hackers will sometimes amplify the flood by using a DNS reflection attack.
This is a multiple-step process:
- The attacker will assume the identity of the victim by forging its IP address.
- Using the forged identity, he will then send out countless DNS queries to an open DNS resolver.
- The DNS resolver processes each query, and then sends the information back to victim device who had its identity stolen. However, the information packets the DNS resolver sends out are much bigger than the queries it receives.
What happens during amplification is that every 1 byte of information becomes 30 or 40 bytes, sometimes even more. Amplify this further using a botnet with a few thousand computers, and you can end up sending 100 gygabytes of traffic towards a site.
How can I defend against DoS/DDoS tools?
Defending against DoS/DDoS attacks can be a challenging task, as these attacks can come from a wide variety of sources and use a range of different techniques to overwhelm your system. However, there are several steps you can take to help protect yourself against these types of attacks:
- Deploy a robust firewall: A firewall is the first line of defense against DoS/DDoS attacks. It helps to block traffic from malicious IP addresses and protect the network infrastructure.
- Use a Content Delivery Network (CDN): A CDN is a network of servers that are distributed around the world. It can help to absorb the traffic and distribute it across multiple servers, reducing the impact of the attack.
- Implement rate-limiting: Rate-limiting is a technique used to limit the amount of traffic that can be sent to a server. It can help to prevent an attacker from overwhelming the server with a flood of requests.
- Utilize intrusion detection/prevention systems: Intrusion detection/prevention systems (IDS/IPS) can help to detect and prevent DoS/DDoS attacks by analyzing network traffic and detecting patterns that indicate an attack is in progress.
- Use a web application firewall (WAF): A WAF is designed to protect web applications from various types of attacks, including DoS/DDoS attacks. It can help to filter out malicious traffic and prevent the server from being overwhelmed.
- Keep software up to date: Keeping software up to date is important to ensure that any vulnerabilities are patched. Vulnerabilities can be exploited by attackers to launch a DoS/DDoS attack.
- Utilize anti-DDoS services: Anti-DDoS services are specifically designed to protect against DoS/DDoS attacks. They can help to identify and block malicious traffic before it reaches the server, minimizing the impact of the attack.
- Develop an incident response plan: Developing an incident response plan is important to minimize the impact of a DoS/DDoS attack. The plan should outline the steps to take in the event of an attack and the roles and responsibilities of each team member.
By following these steps, you can help to defend your system against DoS/DDoS attacks and reduce the risk of a successful attack. However, it is important to remember that no defense is foolproof, and it is always important to have a plan in place to respond quickly in the event of an attack.
FAQ
What is the difference between a DoS attack and a DDoS attack?
A DoS attack is an attack in which a single system or network is overwhelmed with traffic, making it inaccessible to users. A DDoS attack, on the other hand, is a coordinated attack in which multiple systems are used to overwhelm a target system or network.
What are some common motivations for launching a DDoS attack?
Some common motivations for launching a DDoS attack include political activism, financial gain, competitive advantage, and revenge.
How can I tell if my website is being targeted by a DDoS attack?
Some signs that your website may be under a DDoS attack include slow or unresponsive website performance, an increase in spam or suspicious traffic, and unusual patterns of network traffic.
How can I defend against DDoS attacks?
There are several strategies for defending against DDoS attacks, including implementing DDoS protection services, investing in hardware-based protection, conducting regular risk assessments, implementing rate limiting and traffic shaping, and educating employees on security best practices.
Is it illegal to launch a DDoS attack?
Yes, launching a DDoS attack is illegal in most countries and can result in severe legal consequences.
How can I prevent my device from being used as part of a DDoS botnet?
To prevent your device from being used as part of a DDoS botnet, you should keep your software and security patches up to date, avoid downloading suspicious files or programs, and use strong passwords for all accounts.
Can cloud-based services protect against DDoS attacks?
Yes, many cloud-based services offer DDoS protection by using advanced traffic filtering techniques and scalable infrastructure to absorb and mitigate attacks.
How long does a DDoS attack typically last?
The duration of a DDoS attack can vary widely, from a few minutes to several days or even weeks, depending on the size and complexity of the attack and the effectiveness of the defense measures in place.
Can DDoS attacks cause permanent damage to a website or network?
In most cases, DDoS attacks do not cause permanent damage to a website or network. However, they can result in significant downtime and financial losses, as well as damage to a company’s reputation.
Is it possible to trace the source of a DDoS attack?
Tracing the source of a DDoS attack can be difficult, as attackers often use anonymous or spoofed IP addresses to hide their identity. However, with the help of advanced tools and techniques, it is sometimes possible to trace the source of an attack and take legal action against the attackers.
Conclusion
In conclusion, DDoS attacks are a serious threat to websites and online services. These attacks can be launched by anyone with access to the right tools, and can cause significant damage to a business’s reputation, revenue, and user experience. Therefore, it is important for businesses to take proactive measures to defend against these attacks.
There are a variety of tools and techniques that can be used to defend against DDoS attacks. These include deploying firewalls, intrusion detection and prevention systems, load balancers, and content delivery networks. Additionally, businesses should conduct regular vulnerability assessments and penetration testing to identify and remediate any potential weaknesses in their systems.
It is also important for businesses to have a comprehensive incident response plan in place in the event of a DDoS attack. This plan should include clear procedures for detecting and mitigating attacks, as well as communicating with stakeholders and law enforcement.
While it may not be possible to completely eliminate the risk of DDoS attacks, businesses can take proactive steps to reduce their exposure and minimize the impact of any attacks that do occur. By staying vigilant and adopting a proactive security posture, businesses can protect their online presence and maintain the trust of their users.