Wireshark is a powerful network protocol analyzer that allows you to see what’s happening on your network at a microscopic level. Whether you’re a network administrator or just someone who wants to learn more about networking, Wireshark is an essential tool to have in your toolbox. In this tutorial, we’ll go over the basics of how to use Wireshark, including some tips and tricks to help you get the most out of this powerful software.
What is Wireshark?
Wireshark is a free and open-source network protocol analyzer that allows you to see what’s happening on your network. It can capture and analyze network traffic in real-time and display it in a user-friendly format. Wireshark supports a wide range of network protocols, including TCP, UDP, HTTP, DNS, and more.
How does Wireshark work?
Wireshark is a network protocol analyzer that captures and analyzes network traffic in real-time. It works by intercepting the network traffic as it flows between network devices and examining the data contained in each packet.
When you start a Wireshark capture, it puts the network interface into promiscuous mode. In this mode, the interface captures all network traffic that passes through it, not just traffic addressed to the local device. Once Wireshark has captured the traffic, it displays the packets in a user-friendly format, showing information such as the source and destination addresses, the protocol used, and the data contained in the packet.
Wireshark can capture network traffic from a wide range of sources, including wired and wireless networks, and it supports a variety of protocols, including TCP, UDP, HTTP, DNS, and more. It can also decrypt encrypted traffic if it has access to the appropriate keys.
Wireshark provides a powerful set of tools and filters that allow you to analyze the captured network traffic. For example, you can filter the traffic to show only packets from a specific IP address or protocol, or you can use the Follow TCP Stream feature to view the entire TCP stream for a particular connection. Wireshark can also generate statistics about the captured network traffic, and it can even identify potential network problems using the Expert Info feature.
In summary, Wireshark works by intercepting and analyzing network traffic in real-time. It provides a user-friendly interface for examining the packets and a wide range of tools and filters for analyzing the captured data.
When should Wireshark be used?
Wireshark can be used to understand how communication takes place across a network and to analyze what went wrong when an issue in communication arises.
Wireshark helps:
- Network administrators troubleshoot problems across a network
- Security engineers examine security issues across a network
- QA engineers verify applications
- Developers debug protocol implementations
- Network users learn about a specific protocol
When shouldn’t Wireshark be used?
Wireshark can help troubleshoot many network issues, and it can be used as an educational tool. However, Wireshark cannot:
- Help a user who doesn’t understand network protocols: Users must first know how a network operates in order to use Wireshark.
- Grab traffic from locations other than your local computer and the system it talks to: Wireshark cannot grab traffic from all of the other systems on a network.
- Notify you of alerts: The closest Wireshark can do is apply color-coding and show malformed packets.
How to download Wireshark
System Requirements
It is totally safe to install & use Wireshark. Before downloading, firstly go to learn about the system requirements of Wireshark. For Windows, Wireshark requires:
- Any Windows versions that are still in support lifetime
- The Universal C Runtime (included with Windows 10 and Windows Server 2019)
- Any modern 64-bit AMD64/64 or 32-bit processor
- More than 500MB of RAM and disk space
- 1280 × 1024 or higher resolution
For macOS, Wireshark supports macOS 10.14 and later. Starting with Wireshark version 4.0, Apple Silicon hardware is supported. For UNIX and UNIX-like platforms like Linux and most BSD variants, the system specifications are similar to the ones listed for Windows.
Wireshark Download Free
Then follow the guide to get the download file of this tool.
- Go to visit the page https://www.wireshark.org/download.html via a browser.
- You can see the latest version. To download Wireshark for Windows 11/10/8/7 64-bit, click Windows Installer (64-bit) to get an .exe file. To download Wireshark for macOS, click macOS Arm 64-bit .dmg or macOS Intel 64-bit .dmg based on your processor to get a .dmg file.

Wireshark also offers you links to download old versions. Just expand Old Stable Releases, click the download link to get the installation file for Windows (32/64-bit) & macOS based on your operating system. To download Wireshark for Linux, Ubuntu, NetBSD and more, just go to the Third-Party Packages section.
How to Install Wireshark on Windows 11/10/8/7 & macOS
How to install Wireshark on Windows or macOS?
In Windows, double-click on the .exe file to the setup welcome interface, review the license agreement, choose which features you want to install, decide whether to create shortcuts, select the destination folder (by default, it is C:\Program Files\Wireshark), check the box of Install Npcap to capture live network traffic, and the installing process begins. Follow the on-screen instructions to finish the operation.
To install Wireshark on macOS, double-click the .dmg file to open and then you can get a .pkg file. Then, the welcome screen appears. Just follow the instructions on the screen to start the installation.
After downloading & installing Wireshark, now you can use Wireshark to capture network traffic and analyze data on your PC. Just take action if you need this tool.
Wireshark for Linux
Installing Wireshark on Linux can be a little different depending on the Linux distribution. If you aren’t running one of the following distros, please double-check the commands.
Ubuntu
From a Terminal prompt, run these commands:
- sudo apt-get install wireshark
- sudo dpkg-reconfigure wireshark-common
- sudo adduser $USER wireshark
Those commands download and update the package, and add user privileges to run Wireshark.
Red Hat Fedora
From a Terminal prompt, run these commands:
- sudo dnf install wireshark-qt
- sudo usermod -a -G wireshark username
The first command installs the GUI and CLI version of Wireshark, and the second adds permissions to use Wireshark.
Kali Linux
Wireshark is probably already installed because it’s part of the basic package. Check your menu under the option “Sniffing & Spoofing” to verify.
Getting Started with Wireshark
To get started with Wireshark, you’ll first need to download and install it on your computer. Wireshark is available for Windows, macOS, and Linux. Once you’ve installed Wireshark, you can start capturing and analyzing network traffic.
Capturing Network Traffic
To capture network traffic with Wireshark, you’ll first need to select the network interface you want to capture on. This could be your Ethernet interface, Wi-Fi interface, or even a virtual interface created by a virtual machine.
To select the interface, go to the Capture menu and select Options. In the Capture Options window, you can choose the interface you want to capture on. You can also configure other capture options, such as the capture filter and the buffer size.
Once you’ve configured the capture options, you can start capturing network traffic by clicking on the Start button in the main Wireshark window. Wireshark will start capturing network traffic in real-time and display it in the packet list pane.
Analyzing Network Traffic
Once you’ve captured network traffic with Wireshark, you can start analyzing it. Wireshark provides a wide range of tools and filters to help you analyze network traffic.
One of the most useful tools in Wireshark is the filter tool. You can use filters to narrow down the network traffic to specific packets or protocols. For example, you could use a filter to only display HTTP traffic or traffic from a specific IP address.
To apply a filter in Wireshark, simply type the filter in the filter box at the top of the packet list pane. You can also use the filter toolbar to select a filter from a list of commonly used filters.
Wireshark filters
Some of the best features of Wireshark are the capture filters and display filters. Filters allow you to view the capture the way you need to see it to troubleshoot the issues at hand. Below are several filters to get you started.
Wireshark capture filters
Capture filters limit the captured packets by the chosen filter. If the packets don’t match the filter, Wireshark won’t save them. Examples of capture filters include:
host IP-address: This filter limits the captured traffic to and from the IP address
net 192.168.0.0/24: This filter captures all traffic on the subnet
dst host IP-address: Capture packets sent to the specified host
port 53: Capture traffic on port 53 only
port not 53 and not arp: Capture all traffic except DNS and ARP traffic
Wireshark display filters
Wireshark display filters change the view of the capture during analysis. After you’ve stopped the packet capture, use display filters to narrow down the packets in the Packet List to troubleshoot your issue.
One of the most useful display filters is:
ip.src==IP-address and ip.dst==IP-address
This filter shows packets sent from one computer (ip.src) to another (ip.dst). You can also use ip.addr to show packets to and from that IP. Other filters include:
tcp.port eq 25: This filter will show you all traffic on port 25, which is usually SMTP traffic
icmp: This filter will show you only ICMP traffic in the capture, most likely they are pings
ip.addr != IP_address: This filter shows you all traffic except the traffic to or from the specified computer
Analysts even build filters to detect specific attacks, like this filter used to detect the Sasser worm:
Additional Wireshark features
Beyond the capture and filtering, several other features in Wireshark can make your job easier.
Wireshark colorization options
You can configure Wireshark to color your packets in the Packet List according to the display filter, which allows you to emphasize the packets you want to highlight. Check out some examples here.
Wireshark promiscuous mode
By default, Wireshark only captures packets going to and from the computer where it runs. By checking the box to run Wireshark in promiscuous mode in the capture settings, you can capture most of the traffic on the LAN.
Wireshark command line
Wireshark does provide a command line interface (CLI) if you operate a system without a graphical user interface (GUI). The best practice would be to use the CLI to capture and save a log so you can review the log with the GUI.
Wireshark commands
- wireshark : run Wireshark in GUI mode
- wireshark –h : show available command line parameters for Wireshark
- wireshark –a duration:300 –i eth1 –w wireshark. : capture traffic on the ethernet interface one for five minutes. –a means automatically stop the capture, -i specifies which interface to capture
Metrics and statistics
Under the Statistics menu, you’ll find a plethora of options to view details about your capture.
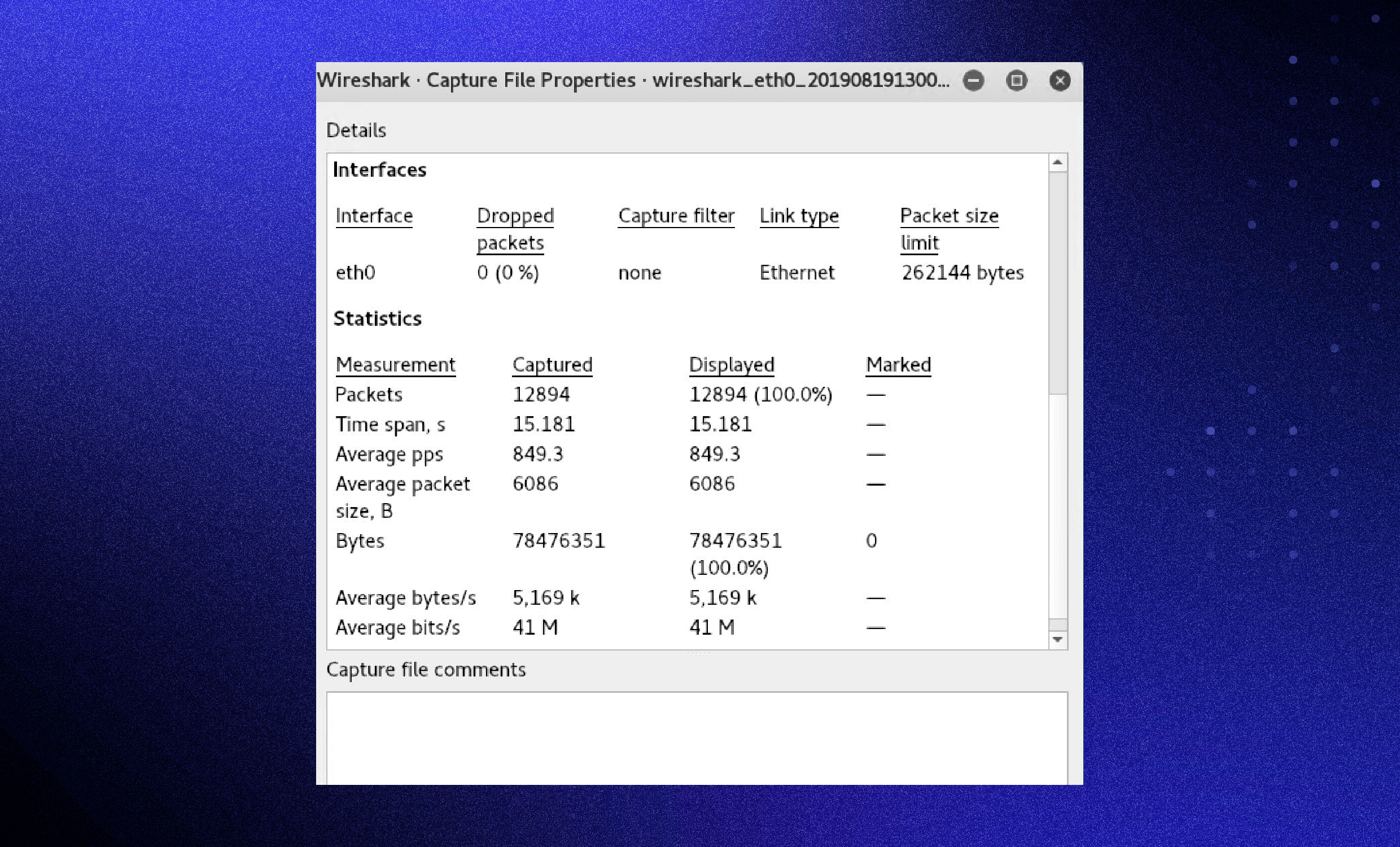
Capture File Properties:
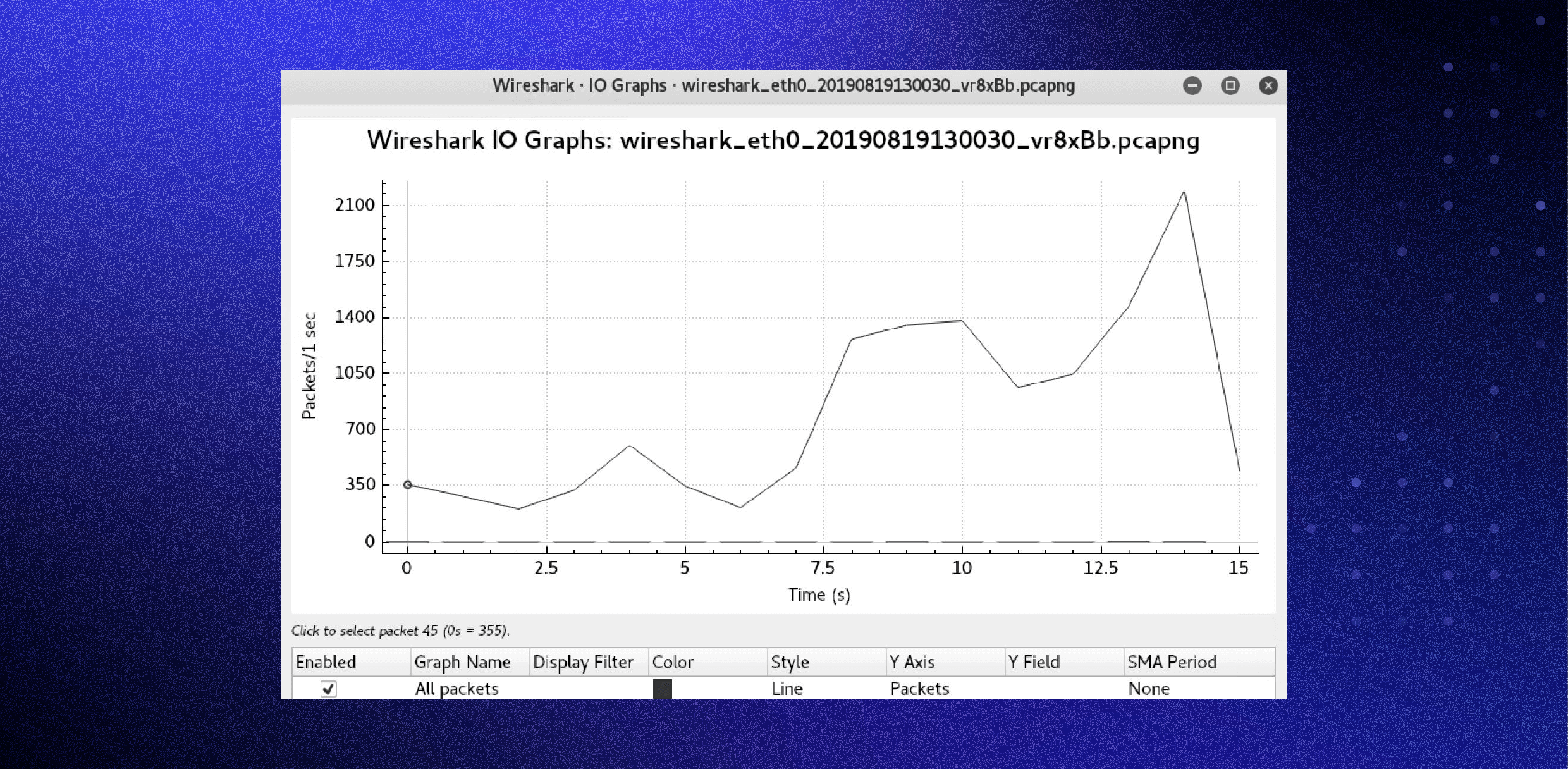
Wireshark I/O Graph:
Additional Wireshark resources and tutorials
There are many tutorials and videos that show you how to use Wireshark for specific purposes. You should begin your search on the main Wireshark website and move forward from there. You can find the official documentation and Wiki on that site as well.
Wireshark is a great network sniffer and analysis tool — however, it’s best used once you know what you’re looking for. You won’t be able to use Wireshark to discover a new problem because there is too much noise on the network
A great example of this is when Varonis security researchers discovered the Norman crypto miner, they received an alert from several machines pointing to suspicious network and file activity. During the analysis of the crypto miner, Varonis researchers used Wireshark to inspect network activities for some of the machines that were misbehaving. Wireshark showed the research team that a new cryptominer, dubbed Norman, was actively communicating to command and control (C&C) servers using DuckDNS. The Varonis team could see all the IP addresses of the C&C servers the attackers used with Wireshark so the company could shut off communication, stopping the attack.
Tips and Tricks for Using Wireshark
Here are some tips and tricks to help you get the most out of Wireshark:
- Use display filters to narrow down the network traffic to specific packets or protocols.
- Use coloring rules to highlight important packets or protocols.
- Use the Follow TCP Stream feature to view the entire TCP stream for a particular connection.
- Use the Statistics menu to generate statistics about the captured network traffic.
- Use the IO Graph feature to visualize network traffic over time.
- Use the Expert Info feature to identify potential network problems.
FAQ
- Q: What is Wireshark used for?
Wireshark is used to capture and analyze network traffic in real-time. It is commonly used for network troubleshooting, security analysis, and protocol development.
- Q: Can Wireshark capture wireless traffic?
Yes, Wireshark can capture wireless traffic as long as it is running on a device with a wireless adapter that supports promiscuous mode.
- Q: Is Wireshark free?
Yes, Wireshark is a free and open-source software tool.
- Q: Can Wireshark decrypt SSL/TLS traffic?
Yes, Wireshark can decrypt SSL/TLS traffic if it has access to the appropriate keys. However, this requires that you have control over both the client and server and can export the keys used for the SSL/TLS session.
- Q: Can Wireshark capture passwords?
Yes, Wireshark can capture passwords and other sensitive information if it is transmitted over an unencrypted protocol, such as HTTP. However, if the data is transmitted over an encrypted protocol, such as HTTPS, Wireshark cannot capture the password unless you have access to the appropriate keys.
- Q: How do I filter packets in Wireshark?
To filter packets in Wireshark, you can use the display filter or capture filter. The display filter allows you to filter packets that are already captured and displayed, while the capture filter allows you to filter packets as they are being captured. You can filter packets by protocol, source or destination IP address, port number, and many other criteria.
- Q: How do I analyze packets in Wireshark?
To analyze packets in Wireshark, you can use the various tools and features provided by the software, such as the packet details pane, the packet list pane, the packet bytes pane, and the statistics window. You can also use the built-in protocol dissectors to analyze the contents of the packets and identify any issues or anomalies.
- Q: Is Wireshark difficult to use?
Wireshark can be complex and overwhelming for beginners, but it provides a comprehensive set of tools and features for advanced users. However, with some practice and experience, anyone can learn to use Wireshark effectively.
Conclusion
Wireshark is a powerful network protocol analyzer that can help you understand what’s happening on your network at a microscopic level. With its wide range of tools and filters, Wireshark is an essential tool for network administrators and anyone who wants to learn more about networking. By following the tips and tricks outlined in this tutorial, you’ll be able to get the most out of this powerful software.













