Hey there, fellow tech enthusiasts! Are you ready to dive into the exciting world of cybersecurity and ethical hacking? Well, you’re in luck because today we’re going to explore the amazing tool that has become a household name in the industry: Kali Linux.
Kali Linux, my friend, is the go-to operating system for those who want to master the art of penetration testing, ethical hacking, and all things cybersecurity. It’s a powerful open-source platform that brings together an extensive collection of tools and resources to help professionals and enthusiasts alike in their quest for digital security.
In this article, we’ll take a closer look at Kali Linux, its origins, and why it has become the top choice for cybersecurity professionals. We’ll delve into its robust toolset, user-friendly interface, and the vibrant community that surrounds it. Plus, we’ll discuss how Kali Linux is used in various domains, from penetration testing and vulnerability assessment to digital forensics and incident response.
But wait, there’s more! We’ll also provide you with valuable insights on getting started with Kali Linux, sharing tips and tricks to help you make the most of this powerful tool. So, whether you’re a curious beginner or a seasoned pro looking to sharpen your skills, this article has got you covered.
So, grab your virtual hard hat, buckle up, and get ready to explore the fascinating world of Kali Linux. By the end of this article, you’ll have a solid understanding of why Kali Linux is the go-to choice for cybersecurity professionals, and you’ll be ready to embark on your own hacking adventures!
What is Kali Linux?
Kali Linux, my friend, is an awesome operating system specially designed for hacking and cybersecurity purposes. It’s like a Swiss Army knife for all the tech-savvy hackers and security professionals out there. With Kali Linux, you get a whole bunch of powerful tools and utilities right at your fingertips, making it a go-to choice for anyone interested in penetration testing, ethical hacking, and all things related to cybersecurity.
You might be wondering, “Why Kali Linux? What’s so special about it?” Well, let me tell you. Kali Linux is jam-packed with pre-installed tools that help you scan, identify vulnerabilities, exploit weaknesses, and secure systems. It’s like having a superhero’s utility belt, but in the form of an operating system.
Whether you’re a cybersecurity enthusiast looking to sharpen your skills or a professional pentester working to protect organizations from cyber threats, Kali Linux has got your back. It offers a wide range of features and capabilities, including scanning and enumeration tools, vulnerability assessment utilities, exploit frameworks, and post-exploitation goodies.
But wait, there’s more! Kali Linux is not just about the tools; it’s also about the community. The Kali Linux community is filled with passionate hackers and security experts who are always ready to lend a helping hand. If you ever get stuck or need some guidance, you can always turn to the community for support and advice.
So, whether you’re a tech geek exploring the depths of cybersecurity or a curious soul wanting to understand how hacking works (for educational purposes, of course), Kali Linux is the perfect playground for you. Just remember to always use it responsibly and ethically, with proper authorization and in compliance with the law.
In a nutshell, Kali Linux is the ultimate playground for hackers and cybersecurity enthusiasts. It’s a powerful operating system packed with tools and a vibrant community, making it the go-to choice for anyone interested in exploring the world of ethical hacking and cybersecurity.
Who uses Kali Linux and Why?

Kali Linux is primarily used by cybersecurity professionals, ethical hackers, penetration testers, and security researchers. It has gained significant popularity in the cybersecurity community for several reasons:
- Penetration Testing and Ethical Hacking: Kali Linux is widely recognized as a powerful tool for conducting penetration testing and ethical hacking activities. Its extensive collection of pre-installed tools, ranging from network scanners to password crackers, makes it an ideal choice for professionals who need a comprehensive platform to assess the security of systems and networks.
- Vulnerability Assessment: Organizations and security professionals use Kali Linux to identify vulnerabilities and weaknesses in their systems and networks. By simulating real-world attacks and exploiting vulnerabilities, they can gain insights into potential risks and take proactive measures to mitigate them.
- Digital Forensics and Incident Response: Kali Linux provides a range of tools for digital forensics and incident response. Security teams and law enforcement agencies use it to investigate and analyze security incidents, gather evidence, and perform forensic analysis on compromised systems.
- Security Education and Training: Kali Linux is widely used in educational settings and training programs to teach cybersecurity concepts, techniques, and best practices. Its user-friendly interface, extensive documentation, and availability of online resources make it a valuable tool for hands-on learning and skill development.
- Security Enthusiasts and Hobbyists: Many security enthusiasts and hobbyists are drawn to Kali Linux for its accessibility, powerful toolset, and the opportunity to explore and learn about cybersecurity. It allows them to experiment with different techniques, test their own systems, and gain a deeper understanding of security principles.
It’s important to note that the use of Kali Linux and similar tools must be done ethically and with proper authorization. Users should always obtain permission to perform security assessments and adhere to legal boundaries, respecting privacy and confidentiality.
Kali Linux is used by cybersecurity professionals, ethical hackers, penetration testers, security researchers, educational institutions, and security enthusiasts. Its comprehensive toolset, community support, and user-friendly nature make it a preferred choice for various security-related activities, including penetration testing, vulnerability assessment, digital forensics, and security education.
Getting Started: How to Install Kali Linux
Alright, my friend, let’s get you started on your Kali Linux journey. Installing Kali Linux is a breeze, and I’ll guide you through the process step by step. So, put on your tech hat, grab a cup of coffee (or your favorite beverage), and let’s dive in!
Step 1: Downloading Kali Linux
First things first, head over to the official Kali Linux website (kali.org) and navigate to the “Downloads” section. Here, you’ll find different versions and flavors of Kali Linux. Choose the one that suits your needs and click on the download link. It’s usually a hefty file, so make sure you have a stable internet connection and some patience.
Step 2: Preparing the Installation Media
While the Kali Linux download is in progress, let’s prepare the installation media. You have a couple of options here. You can either create a bootable USB drive or set up a virtual machine to run Kali Linux. If you’re new to this, I recommend going the virtual machine route as it’s more beginner-friendly.
For a bootable USB drive, you’ll need a tool like Rufus (for Windows) or Etcher (for macOS and Linux). Simply launch the tool, select the Kali Linux ISO file you downloaded, choose your USB drive, and let the magic happen.
If you prefer a virtual machine, software like VirtualBox or VMware Player is your go-to choice. Install the virtualization software, create a new virtual machine, and when prompted, select the Kali Linux ISO file as your virtual machine’s bootable media.
Step 3: Installing Kali Linux
Now that you have your installation media ready, it’s time to install Kali Linux. If you’re using a USB drive, plug it into your computer and restart. Make sure your system is set to boot from the USB drive in the BIOS settings. Once it boots up, you’ll be greeted with the Kali Linux installation menu. Follow the on-screen instructions, choose your preferred language, and select the installation type (usually a graphical installation).
If you’re running Kali Linux in a virtual machine, fire up the virtualization software, select your Kali Linux virtual machine, and click the “Start” button. This will launch the installation process within the virtual machine, where you’ll go through similar steps as the USB drive installation.
Step 4: Configuration and Setup
After the installation completes, your system will reboot, and you’ll be welcomed into the world of Kali Linux. Hooray! Now, it’s time to set up your user account, password, and other configuration settings. Follow the on-screen instructions to create your user account and set up the necessary details.
Once the setup is complete, you’re all set to explore Kali Linux and its amazing array of tools. Spend some time familiarizing yourself with the interface, browsing through the installed tools, and getting a feel for the operating system.
Congratulations, my friend! You’ve successfully installed Kali Linux on your system or set it up in a virtual machine. Now, you’re ready to unleash your inner hacker and delve into the exciting world of cybersecurity. Remember to use Kali Linux responsibly, always staying within legal and ethical boundaries.
Mistakes To Avoid With Kali Linux

Hey there, my fellow Kali Linux adventurer! As you embark on your journey with this powerful operating system, it’s essential to know about some common mistakes that people make. So, let’s buckle up and make sure you steer clear of these pitfalls. Trust me, it’ll save you a lot of headaches along the way!
Mistake 1: Not Updating Regularly
Ah, the excitement of exploring new tools and features in Kali Linux can make you forget about updates. But hey, don’t fall into that trap! It’s crucial to keep your Kali Linux system up to date. Updates often bring security patches, bug fixes, and new functionalities, ensuring that you have the best and most secure experience. So, make it a habit to regularly update your Kali Linux system.
Mistake 2: Neglecting Documentation and Tutorials
Kali Linux is a beast, my friend, and taming this beast requires some knowledge and understanding. One mistake many people make is skipping the documentation and tutorials. Don’t be that person! Take the time to read the official Kali Linux documentation, explore online tutorials, and join forums or communities to learn from experienced users. It will save you from a lot of confusion and help you make the most of Kali Linux’s capabilities.
Mistake 3: Not Backing Up Your Data
Oops! Imagine spending hours tweaking and configuring your Kali Linux setup, only to encounter a system crash or accidental deletion of important files. Trust me, it’s a nightmare you don’t want to experience. Always back up your important data and configurations regularly. This way, even if something goes wrong, you can quickly restore your system and get back on track without starting from scratch.
Mistake 4: Running Unauthorized Tests
Listen up, my friend: ethical hacking and penetration testing must always be conducted with proper authorization. Don’t go poking around other people’s systems without permission. Running unauthorized tests is not only unethical but also illegal in many jurisdictions. Always ensure you have the proper authorization and consent before conducting any security assessments or tests using Kali Linux.
Mistake 5: Overlooking Security Best Practices
Now, here’s an important one: don’t forget about security best practices! It’s easy to get caught up in the excitement of hacking and forget about securing your own Kali Linux system. Remember to enable firewalls, use strong and unique passwords, practice good network hygiene, and keep an eye on potential vulnerabilities in your own setup. After all, you want to protect your Kali Linux system from any potential threats, right?
By avoiding these common mistakes, you’ll have a smoother and more enjoyable experience with Kali Linux. Stay updated, explore documentation and tutorials, back up your data, always seek proper authorization, and prioritize security best practices. With these precautions in mind, you’ll be well on your way to mastering Kali Linux and becoming a cybersecurity ninja!
Using Kali Linux: Finding Tools

Hey there, my friend! So, you’ve got Kali Linux up and running, and now you’re probably wondering, “Where do I find all those awesome tools?” Well, fear not, because I’m here to guide you through the process of finding tools in Kali Linux. Let’s dive right in!
When it comes to Kali Linux, it’s like having a treasure trove of hacking and cybersecurity tools at your disposal. Here’s how you can find and access them:
- Menu: The Kali Linux menu is your gateway to a world of tools. Just click on the Kali dragon icon in the top left corner, and a menu will pop up, showing various categories. You’ll find tools categorized under sections like Information Gathering, Vulnerability Analysis, Exploitation Tools, Wireless Attacks, and much more. Simply explore the menu and click on the tool you want to use.
- Terminal: Ah, the good ol’ terminal! If you’re familiar with the command line, you can easily find and run tools using the terminal in Kali Linux. Open the terminal by clicking on the terminal icon in the taskbar or by pressing Ctrl+Alt+T. Once the terminal is open, you can use commands like
apt,apt-get, oraptitudeto search for and install tools. For example, to search for a tool called “nmap,” you can use the commandapt search nmaporapt-get search nmap. - Tools Directory: Kali Linux has a dedicated directory where all the installed tools are stored. You can access this directory by navigating to
/usr/share/and then exploring the subdirectories for different tool categories. For example, you’ll find tools related to web application testing in/usr/share/webshells/. Feel free to browse around and find the tools that pique your interest. - Online Resources: Kali Linux has an extensive community and online resources that can help you discover even more tools. You can visit the official Kali Linux website, join forums, explore blogs and tutorials, and participate in discussions to uncover hidden gems and recommendations from experienced users.
Remember, my friend, the Kali Linux tools are powerful, so always use them responsibly and within the bounds of legality and ethics. Ensure that you have proper authorization and consent before using the tools on any system or network.
Absolutely, my friend! For beginners in the world of penetration testing, it can indeed be overwhelming to navigate through the extensive list of tools in Kali Linux. To make it easier for you, here’s a breakdown of common pentest tasks and the corresponding Kali Linux tools you can use:
Scanning and Enumeration:
- Task: Discovering hosts, open ports, and services.
- Kali Linux Tools: Nmap, Netdiscover, SNMPWalk.
Vulnerability Assessment:
- Task: Identifying vulnerabilities in target systems.
- Kali Linux Tools: OpenVAS, Nexpose, Nikto.
Exploitation:
- Task: Exploiting identified vulnerabilities to gain unauthorized access.
- Kali Linux Tools: Metasploit Framework, SQLMap, Armitage.
Wireless Attacks:
- Task: Assessing wireless networks and exploiting weaknesses.
- Kali Linux Tools: Aircrack-ng, Reaver, Fern Wifi Cracker.
Web Application Testing:
- Task: Assessing the security of web applications.
- Kali Linux Tools: Burp Suite, OWASP ZAP, wpscan.
Password Attacks:
- Task: Cracking passwords and gaining unauthorized access.
- Kali Linux Tools: John the Ripper, Hydra, Hashcat.
Social Engineering:
- Task: Manipulating human behavior to gain unauthorized access.
- Kali Linux Tools: Social Engineering Toolkit (SET), Maltego, BeEF.
Post-Exploitation:
- Task: Maintaining access, escalating privileges, and gathering information.
- Kali Linux Tools: Meterpreter, Empire, BeEF.
Remember, my friend, this is just a sample of common pentest tasks and the corresponding Kali Linux tools. The world of penetration testing is vast, and there are many more tools and techniques to explore. It’s essential to have a solid understanding of the fundamentals and to continually expand your knowledge as you gain experience.
Don’t hesitate to refer to Kali Linux documentation, online tutorials, and the supportive community to learn more about these tools and their usage. And always remember to use these tools responsibly, with proper authorization and compliance with the law.
Using a Pentesting Framework
Hey there, my friend! So, you’re ready to level up your penetration testing game and dive into the world of using a pentesting framework with Kali Linux? That’s awesome! Let’s talk about how you can harness the power of a pentesting framework and make your life a whole lot easier.
In the realm of pentesting, a framework acts as a powerhouse that brings together various tools, functionalities, and methodologies in one cohesive package. It streamlines your workflow, simplifies complex tasks, and allows you to focus on the fun part—uncovering vulnerabilities and securing systems.
Kali Linux has one of the most popular pentesting frameworks out there, called Metasploit Framework. Here’s how you can make the most of it:
Getting Familiar:
First things first, let’s get acquainted with Metasploit Framework. Open up your terminal in Kali Linux and type msfconsole to launch the framework. You’ll be greeted with a powerful command-line interface where you can interact with Metasploit.
Exploring Modules:
Metasploit Framework is all about modules—predefined pieces of code that help you perform specific tasks. These modules range from exploit modules to post-exploitation modules, and more. You can explore available modules by using the search command within the framework. For example, search exploit will display a list of exploit modules you can use.
Configuring and Customizing:
Metasploit Framework allows you to configure various settings and options according to your needs. Take some time to explore the configuration files and customize the framework to match your preferences. You can find the configuration files in the /usr/share/metasploit-framework/config directory.
Exploiting Vulnerabilities:
One of the primary functions of Metasploit Framework is exploiting vulnerabilities. You can use exploit modules to launch targeted attacks on vulnerable systems. Remember, always ensure you have proper authorization and consent before using any exploit modules.
Post-Exploitation:
After successfully exploiting a target, Metasploit Framework provides post-exploitation modules that help you maintain access, escalate privileges, and gather valuable information from the compromised system. These modules are essential for simulating real-world attack scenarios.
Documentation and Community:
Metasploit Framework is a powerful tool with extensive documentation and a supportive community. Take advantage of the official Metasploit documentation, forums, blogs, and tutorials to expand your knowledge, learn new techniques, and troubleshoot any issues you may encounter.
Remember, my friend, using a pentesting framework like Metasploit is just one aspect of penetration testing. It’s important to have a solid understanding of the underlying concepts, techniques, and methodologies. Continuously expand your knowledge and keep up with the latest trends in the ever-evolving field of cybersecurity.
So, go forth, explore Metasploit Framework, and embrace the power it brings to your pentesting adventures. Happy hacking, and may you uncover vulnerabilities that make systems stronger!
Step 1: Defining Scope and Goals

Before you dive headfirst into your pentesting adventure with Kali Linux, it’s crucial to start with the first step: defining the scope and goals of your testing. This step helps you set boundaries, determine what you’re trying to achieve, and ensure that your efforts are focused and effective.
Defining the scope involves identifying the systems, networks, or applications that will be included in your pentest. This helps you avoid accidentally targeting unauthorized systems and ensures that you stay within legal and ethical boundaries. Think of it as drawing a map of your exploration.
When it comes to goals, you want to clearly define what you aim to achieve through your pentesting efforts. Are you focused on identifying vulnerabilities, testing the effectiveness of security controls, or simulating real-world attack scenarios? By setting specific goals, you can tailor your approach and prioritize your efforts accordingly.
Now, let’s talk about different approaches to pentesting: black box, white box, and gray box. These approaches determine the level of information and access you have to the target system.
- Black Box Testing: In black box testing, you have no prior knowledge or access to the target system. It’s like going into a test blindfolded, relying solely on your skills and tools to identify vulnerabilities. This approach simulates a real-world scenario where an attacker has no insider information.
- White Box Testing: In white box testing, you have complete knowledge and access to the target system. It’s like having all the keys to the kingdom! This approach allows you to assess the system’s security controls thoroughly and identify vulnerabilities from an insider’s perspective.
- Gray Box Testing: Gray box testing is a mix of black box and white box approaches. Here, you have partial knowledge or access to the target system. It’s like having a peek through a slightly opened door. This approach can be useful when you want to simulate an insider attack or assess specific areas while keeping some elements unknown.
When defining the scope and goals, consider which approach aligns best with your objectives and the resources available to you. Remember, transparency, communication, and proper authorization are key throughout the process to ensure a smooth and ethical pentesting engagement.
Step 2: Recon and OSINT

Alright, my friend, now that we have defined the scope and goals of our pentesting adventure, it’s time to move on to the next step: Reconnaissance and OSINT. This step involves gathering valuable information about the target system, network, or organization, just like a detective collecting clues.
Reconnaissance, or recon for short, is the process of actively searching for information about the target. OSINT, which stands for Open Source Intelligence, refers to gathering information from publicly available sources. Both of these activities provide a solid foundation for your pentesting efforts.
Now, let’s see how Kali Linux can be your trusty sidekick during the recon and OSINT phase:
- Passive Recon: During passive recon, you gather information without directly interacting with the target. You can use tools like Shodan, Recon-ng, and Maltego in Kali Linux to search for public information, discover exposed services, and map out the network topology. This helps you build a picture of the target’s digital footprint and potential vulnerabilities.
- Active Recon: Active recon involves more direct interactions with the target system or network. Here, tools like Nmap, the Swiss Army knife of network scanning, come in handy. Nmap allows you to scan for open ports, identify live hosts, and gather information about the services running on those hosts. With Kali Linux, you can unleash the power of Nmap and get insights into the target’s infrastructure.
- OSINT Techniques: OSINT goes beyond technical reconnaissance. It involves digging into publicly available information, such as social media profiles, company websites, and news articles, to gather insights about the target organization. Kali Linux provides tools like theHarvester and SpiderFoot, which automate the process of gathering information from various online sources.
Remember, my friend, the recon and OSINT phase helps you understand the target better, identify potential entry points, and tailor your pentesting approach. It’s important to always conduct recon and OSINT activities in a legal and ethical manner, respecting privacy and abiding by relevant laws and regulations.
Step 3: Scan and Discover

now it’s time to move on to the next step of our pentesting adventure with Kali Linux: scanning and discovery. This phase is where the real fun begins as we actively probe the target system or network to uncover vulnerabilities and potential entry points.
In this step, we’ll be using Kali Linux’s powerful scanning tools to gather more detailed information about the target. So, grab your virtual magnifying glass and let’s get started!
- Nmap: Ah, Nmap, the holy grail of scanning tools! With Kali Linux, you have this Swiss Army knife of network scanning right at your fingertips. Nmap allows you to discover open ports, identify live hosts, and even fingerprint the operating systems running on those hosts. So, fire up your terminal and unleash the power of Nmap to gather crucial information about the target’s network infrastructure.
- Nessus: Another valuable tool in Kali Linux’s arsenal is Nessus, a comprehensive vulnerability scanner. Nessus helps you identify potential security weaknesses, misconfigurations, and known vulnerabilities in the target systems. By running Nessus scans, you can gain a deeper understanding of the target’s security posture and pinpoint areas that require further investigation.
- Nikto: When it comes to web application scanning, Nikto is your go-to tool in Kali Linux. It specializes in scanning web servers and identifying common vulnerabilities and misconfigurations. By running Nikto against the target’s web applications, you can uncover potential weaknesses and vulnerabilities that attackers could exploit.
- OpenVAS: OpenVAS (Open Vulnerability Assessment System) is a powerful vulnerability scanner available in Kali Linux. It allows you to perform comprehensive vulnerability assessments, scanning for a wide range of known vulnerabilities in the target systems. OpenVAS provides detailed reports on discovered vulnerabilities, aiding you in prioritizing your efforts and developing effective mitigation strategies.
Remember, my friend, scanning and discovery are critical steps in the pentesting process. However, it’s crucial to conduct these activities with proper authorization and adhere to ethical guidelines. Always ensure you have the necessary permissions to scan and assess the target systems, and be mindful of any potential impact your scanning activities may have on the target’s network.
Step 4: Gain Unauthorized Access and Exploit

My intrepid pentester! We’ve reached an exciting phase in our Kali Linux-powered pentesting adventure: gaining unauthorized access and exploiting vulnerabilities. Now, let’s put our skills to the test and see how we can leverage Kali Linux to breach the target system’s defenses.
Disclaimer: Remember, my friend, it’s essential to always conduct pentesting activities ethically and with proper authorization. Only perform these steps on systems you have explicit permission to test.
- Metasploit Framework: Oh, Metasploit, the crown jewel of Kali Linux’s hacking arsenal! This powerful framework allows you to launch targeted attacks, exploit vulnerabilities, and gain unauthorized access to the target system. With its vast collection of exploit modules, Metasploit provides an extensive range of options to suit your specific needs. Fire up the Metasploit console using the
msfconsolecommand and let the hacking fun begin! - Social Engineering Toolkit (SET): Sometimes, the weakest link in a system’s security is not a technical vulnerability but rather the human factor. This is where the Social Engineering Toolkit (SET) in Kali Linux comes into play. SET allows you to craft phishing emails, create malicious websites, and perform various social engineering attacks to trick users into revealing sensitive information or gaining access to their systems.
- Password Attacks: Cracking passwords is a classic tactic used to gain unauthorized access. Kali Linux provides a range of tools for password attacks, such as John the Ripper, Hydra, and Hashcat. These tools leverage various techniques like brute-force, dictionary, and rainbow table attacks to crack passwords and gain entry to protected accounts.
- Exploiting Web Applications: Web applications are often prime targets for exploitation. Kali Linux offers tools like SQLMap and Burp Suite to help identify and exploit vulnerabilities in web applications. SQLMap specializes in detecting and exploiting SQL injection vulnerabilities, while Burp Suite provides a comprehensive suite of tools for analyzing and manipulating web traffic.
Remember, my friend, with great power comes great responsibility. It’s crucial to always use these techniques and tools ethically, with proper authorization and consent. Additionally, document and communicate any findings responsibly to the relevant stakeholders.
Pentesting is about finding vulnerabilities and helping organizations improve their security, not causing harm. So, stay ethical, be mindful of your actions, and use your powers for good.
Step 5: Post-exploitation
After exploiting a vulnerability and compromising a network, you may want to show what you can do with it to your customers to prove the impact and the risks associated with the breach.
Metasploit has tons of modules for this purpose, but you can open the interactive menu of Kali Linux to get the full list of post-exploitation tools available:
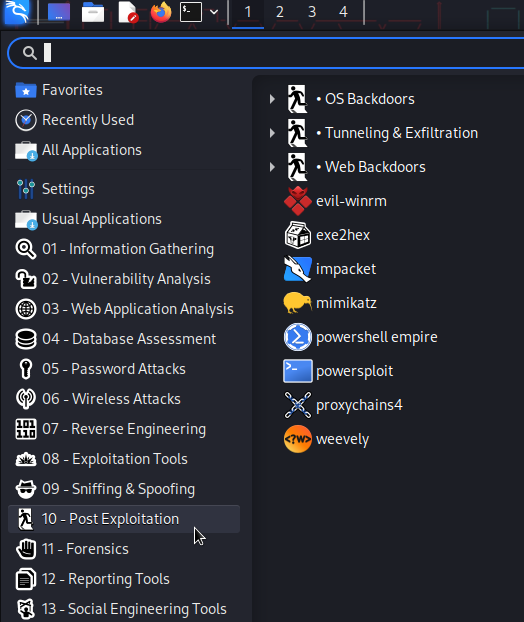
If it’s a Windows/Active directory environment, Kali has several packages for that, like Mimikatz, a small but powerful utility for Kerberoasting and password dumping, or Impacket, a set of scripts to attack.
Depending on the brief and the size of the organization, you may have to get further access, and progress from the system you’ve just compromised to another.
This technique is called pivoting. You may have to demonstrate that you can maintain access and get deeper into the targeted infrastructure.
Step 6: Clean Up Your Mess
As we near the end of our Kali Linux-powered pentesting adventure, it’s time to address an important step: cleaning up your mess. After you’ve completed your testing and gathered the necessary information, it’s crucial to leave the target system in a secure and stable state. Let’s go through the steps to tidy things up properly:
- Remove Backdoors and Malicious Artifacts: As an ethical hacker, it’s vital to remove any backdoors or malicious artifacts you may have introduced during the testing process. This ensures that the target system remains secure and free from any potential vulnerabilities or unauthorized access points. Use tools like Metasploit’s Meterpreter or Empire to clean up your tracks and remove any traces of your presence.
- Reinstate Security Controls: During the testing phase, you may have disabled or bypassed certain security controls to carry out your activities. As part of the cleanup process, make sure to reinstate these controls to their original state. This helps maintain the security posture of the target system and ensures that it remains protected from potential threats.
- Document and Report Findings: It’s essential to document your findings, including the vulnerabilities discovered and any potential risks identified. Prepare a detailed report that outlines the testing process, the vulnerabilities exploited, and recommendations for remediation. This report will be crucial for the target organization to understand the security gaps and take appropriate actions to address them.
- Engage in Post-Engagement Communication: Once you’ve completed your testing and prepared the report, engage in post-engagement communication with the target organization. Discuss your findings, answer any questions they may have, and provide guidance on how to remediate the identified vulnerabilities. This communication helps ensure a smooth transition and fosters a collaborative approach to improving security.
Remember, my friend, the cleanup phase is just as important as the testing itself. It demonstrates your professionalism, ethical conduct, and commitment to security. By properly cleaning up after your testing, you help the target organization strengthen its defenses and safeguard against potential future attacks.
Step 7: Report and Make Recommendations
We’ve reached the final step of our Kali Linux-powered pentesting adventure: reporting and making recommendations. This step is all about effectively communicating your findings and providing actionable suggestions to improve the target organization’s security posture. So, let’s dive into it!
- Document Your Findings: First things first, gather all your notes, reports, and evidence from the pentesting process. Make sure you have a comprehensive record of the vulnerabilities discovered, the techniques used, and any potential risks identified. This documentation forms the foundation of your report.
- Prepare a Detailed Report: Now, it’s time to compile all the information into a well-structured and clear report. Use a professional tone and provide an executive summary highlighting the key findings and their potential impact. Include a detailed breakdown of each vulnerability, its severity, and recommendations for remediation. Organize the report in a way that is easy to understand for both technical and non-technical stakeholders.
- Prioritize Recommendations: Not all vulnerabilities are created equal, my friend. As part of your report, prioritize the recommendations based on their severity and potential impact. Highlight critical vulnerabilities that require immediate attention, and provide a roadmap for addressing other identified issues. This helps the target organization allocate resources effectively and tackle the most pressing security concerns first.
- Provide Actionable Suggestions: Don’t just identify problems—be the solution! Alongside each vulnerability, provide clear and actionable suggestions for remediation. Offer best practices, security controls, and specific steps that the organization can take to mitigate the identified risks. This demonstrates your expertise and shows that you’re genuinely invested in improving their security.
- Follow Up and Support: Pentesting doesn’t end with the report. Stay engaged with the target organization and offer your support as they implement the recommended changes. Answer any questions they may have, clarify technical aspects, and provide guidance throughout the remediation process. This level of support builds trust and helps ensure the effectiveness of your recommendations.
Remember, my friend, effective reporting and making recommendations are key to the success of your pentesting engagement. By delivering a well-crafted report with actionable suggestions, you contribute to enhancing the overall security posture of the target organization.
Open-source Alternatives to Kali Linux

So you’re curious about open-source alternatives to Kali Linux? I got you covered! While Kali Linux is a fantastic tool for pentesting and cybersecurity, there are a few other open-source options you can explore. Let’s take a look
Parrot OS
Parrot OS is a fantastic open-source alternative to Kali Linux that deserves a closer look. Designed with a focus on security, privacy, and development, Parrot OS offers a user-friendly interface and a range of pre-installed tools for various purposes.
One of the notable features of Parrot OS is its lightweight nature, making it suitable for running on lower-end hardware without compromising performance. It’s also designed to prioritize privacy-enhanced features, providing users with tools and configurations that promote secure communication and protect their online activities.
Parrot OS comes with a diverse set of tools for penetration testing, digital forensics, cryptography, reverse engineering, and more. It offers an extensive repository of security-related packages, allowing users to easily install and update the tools they need for their specific tasks.
Additionally, Parrot OS supports a range of desktop environments, including the popular MATE and KDE Plasma, giving users the flexibility to choose an interface that suits their preferences. It also provides a variety of specialized editions, such as Parrot Security, Home, IoT, and Cloud, catering to different user needs.
The Parrot OS community is vibrant and active, providing support and resources to help users get started and navigate their way through the system. The project is committed to open-source principles and encourages collaboration and contributions from the community.
Black Arch Linux
BlackArch Linux is a noteworthy open-source alternative to Kali Linux that is specifically focused on providing a vast collection of penetration testing and security-related tools. Based on the Arch Linux distribution, BlackArch Linux offers a comprehensive repository of over 2,000 tools for various cybersecurity tasks.
The primary aim of BlackArch Linux is to provide penetration testers, security researchers, and ethical hackers with an extensive range of specialized tools to aid in their testing and analysis activities. From network scanning and vulnerability assessment to password cracking and digital forensics, BlackArch Linux covers a wide array of cybersecurity domains.
As an Arch Linux-based distribution, BlackArch Linux offers a rolling release model, which means you can continuously update your system and have access to the latest tool versions and security patches. This ensures that you have the most up-to-date tools at your disposal to tackle evolving cybersecurity challenges.
BlackArch Linux also provides a convenient command-line tool called “blackman” that simplifies the installation and management of tools from its repository. This makes it easy to customize your system and select the specific tools you need for your pentesting or security assessment tasks.
With its dedicated community of users and developers, BlackArch Linux fosters a collaborative environment where users can share knowledge, seek support, and contribute to the improvement of the distribution. This vibrant community adds to the value and usability of BlackArch Linux as a powerful toolset for cybersecurity professionals.
So, if you’re seeking a specialized open-source distribution with an extensive repository of penetration testing and security tools, BlackArch Linux is a great choice. Explore its vast collection, stay updated with the rolling release model, and engage with the supportive community to enhance your skills and expand your cybersecurity expertise.
BackBox
BackBox is a popular open-source Linux distribution specifically designed for penetration testing, ethical hacking, and cybersecurity assessment. It provides a comprehensive set of tools and resources to support professionals in their security testing endeavors.
BackBox is built on the Ubuntu operating system, known for its user-friendly interface and stability. It offers a range of pre-installed security tools, making it easy for users to get started with their pentesting activities. The distribution aims to provide a well-rounded toolkit that covers various aspects of security testing, including vulnerability assessment, network analysis, web application testing, and more.
One of the distinguishing features of BackBox is its emphasis on simplicity and ease of use. The distribution strives to offer a streamlined and intuitive experience, allowing users to focus on their testing tasks without unnecessary complexity. This makes it suitable for both beginners and experienced professionals in the field.
BackBox also promotes a collaborative approach by encouraging community involvement. Users can contribute to the development of the distribution, share their knowledge and experiences, and participate in discussions with fellow security enthusiasts through the BackBox forums and community resources.
Furthermore, BackBox emphasizes compatibility with other open-source security tools and frameworks, enabling users to extend their toolkit and integrate with existing workflows seamlessly. This flexibility makes it a versatile choice for various pentesting scenarios.
Fedora Security Lab
Fedora Security Lab is a specialized variant of the Fedora operating system that focuses on providing a comprehensive set of security tools and resources. It is designed to support professionals and enthusiasts in the field of cybersecurity, penetration testing, and digital forensics.
As a part of the Fedora ecosystem, Fedora Security Lab benefits from the stability, performance, and community support that Fedora offers. It is built on the latest version of Fedora, ensuring access to the most up-to-date software packages and security updates.
Fedora Security Lab comes with a wide range of pre-installed security tools, including vulnerability scanners, network analyzers, password crackers, malware analysis tools, and encryption utilities. These tools are carefully curated to cover various aspects of security testing and research.
The distribution provides an easy-to-use interface and a streamlined environment that facilitates efficient navigation and tool usage. It aims to offer a smooth user experience while ensuring that all necessary tools are readily available for security testing and analysis.
As an open-source project, Fedora Security Lab benefits from the collaborative nature of the Fedora community. Users can participate in discussions, share their expertise, contribute to the development of the distribution, and provide feedback to help improve the security toolset.
One of the notable advantages of Fedora Security Lab is its integration with the vast Fedora software repositories. Users have access to a wide range of additional packages and tools beyond the pre-installed ones, enabling them to customize their security testing environment according to their specific needs.
If you are interested in exploring a comprehensive security-focused Linux distribution, Fedora Security Lab provides a solid foundation. It combines the stability and community support of Fedora with a curated selection of security tools, offering a powerful platform for cybersecurity professionals and enthusiasts alike.
Resources for Kali Linux Training
Hey there, my friend! If you’re looking to level up your skills in Kali Linux, there are plenty of resources available to help you on your journey. Here are some great options to consider:
- Official Kali Linux Documentation: The official Kali Linux website provides comprehensive documentation that covers various aspects of the operating system, including installation, configuration, and usage of its tools. It’s a fantastic starting point to familiarize yourself with Kali Linux and its capabilities.
- Online Tutorials and Blogs: Many online platforms offer tutorials and blog posts specifically dedicated to Kali Linux. Websites like Null Byte, Hackaday, and Medium have a wealth of tutorials, walkthroughs, and tips to help you learn different techniques, tools, and methodologies in Kali Linux.
- YouTube Videos and Channels: YouTube is a treasure trove of Kali Linux tutorials and demonstrations. Channels like “The Cyber Mentor,” “Hak5,” and “IppSec” provide in-depth videos covering various topics, ranging from basic usage to advanced penetration testing techniques. Watching video tutorials can be a great way to see Kali Linux in action and learn from experienced practitioners.
- Online Courses and Training Platforms: Several online learning platforms offer dedicated courses on Kali Linux and ethical hacking. Websites like Udemy, Coursera, and Offensive Security’s “OffSec Academy” provide structured training programs with hands-on exercises, practical labs, and certifications. These courses can give you a more structured and guided learning experience.
- Kali Linux Community and Forums: Engaging with the Kali Linux community can be a valuable learning resource. Joining forums like the Kali Linux Community Forums and subreddits like r/Kalilinux allows you to connect with like-minded individuals, ask questions, and learn from their experiences. It’s a great way to expand your knowledge and network with other Kali Linux enthusiasts.
Remember, my friend, learning Kali Linux is an ongoing process. Practice, hands-on experience, and staying up to date with the latest tools and techniques are key. So, dive into these resources, experiment with Kali Linux in your own lab environment, and keep pushing your boundaries as you become a skilled practitioner in the exciting world of ethical hacking and penetration testing!
Bottom Line: Kali Linux
In conclusion, Kali Linux is a powerful open-source operating system designed for ethical hacking, penetration testing, and cybersecurity assessments. With its extensive collection of pre-installed tools and a robust community, Kali Linux provides a comprehensive platform for professionals and enthusiasts in the field.
Whether you’re a seasoned security expert or just starting your journey, Kali Linux offers a range of features and resources to support your endeavors. Its tools cover various aspects of security testing, including network scanning, vulnerability assessment, web application testing, password cracking, and more.
Kali Linux’s user-friendly interface, extensive documentation, and online resources make it accessible to users of different skill levels. The operating system’s rolling release model ensures that you have access to the latest tool versions and security updates, keeping you up to date with the evolving cybersecurity landscape.
As an open-source project, Kali Linux benefits from a collaborative community that actively contributes to its development, shares knowledge, and provides support to fellow users. This vibrant community enhances the overall experience and fosters continuous learning and improvement.
However, it’s important to remember that using Kali Linux or any other similar tools must be done ethically and with proper authorization. Respect privacy, adhere to legal boundaries, and always obtain the necessary permissions before conducting any security assessments or penetration testing activities.
So, whether you’re looking to sharpen your hacking skills, enhance your security testing capabilities, or simply explore the world of cybersecurity, Kali Linux is a top choice. Embrace its power, dive into the available resources, and embark on your journey to becoming a skilled ethical hacker or penetration tester!













