Hacking ≠ Exploitation — The True Hacker Mindset | Codelivly
Discover why hacking doesn't mean exploitation — learn the hacker mindset, differences between white/black/grey hats, and how curiosity improves security. You know the scene: a shadowy figure in a dark room, typing furiously as green code floods the screen. They're breaking into the "mainframe," causing...
Hardware Hacking: Tools, Attacks, Detection & Ethical Uses
Explore hardware hacking tools, common attacks, detection methods, and ethical applications — a practical guide for security pros and curious makers. Its history dates back to the 1970s and 1980s, when personal computing became more widespread and accessible. Today, hardware hacking has evolved into a...
Network Forensics 101: Tools, Techniques & Analysis
Learn network forensics basics, tools, techniques, log analysis & packet capture methods. Ideal guide for cybersecurity learners and incident responders. There are many systems that track and record network activities and data. However, there are still some measures that add up to the forensics on...
Metasploit for Ethical Pen-Testing: Secure & Harden Websites
Learn how security pros use Metasploit ethically — authorized pen-testing workflows, defensive checks, and website hardening steps to reduce real vulnerabilities. Normally, a penetration tester or hacker uses Metasploit to exploit vulnerable services in a target server or to create a payload to set up...
Threat Hunting — Practical Guide (Part 2) | Codelivly
Part 2 of "Hunt Evil": hands-on threat-hunting techniques, detection workflows, tools, and real case examples to help you find and remediate advanced network threats. As we discussed in the Part 1 , adversaries will come in many forms and will deploya wide variety of different...
Threat Hunting — Practical Guide (Part 1) | Codelivly
Part 1 of "Hunt Evil": foundational threat-hunting concepts, triage workflows, key data sources, and essential tools to start detecting advanced network threats You might have heard a lot of buzz around this topic of “Threat Hunting” and want to try your hand at proactive detection....
Chinese Hackers & AI Agents Target Cloud & Telecom
A Investigative report on Chinese-linked hacking groups and autonomous AI agents targeting global cloud and telecom infrastructure — tactics, impact, and mitigation. A series of new reports from leading cybersecurity firms paints a concerning picture of the evolving digital threat landscape. Nation-state hackers from China...
AI Hacking Teams Now Autonomously Exploit “Zero-Day” Vulnerabilities, Research Reveals
A groundbreaking new study demonstrates that teams of LLM agents can find and exploit previously unknown security flaws without human guidance, as experts warn enterprise AI assistants are wide open to a devastating "zero-click" takeover. LAS VEGAS, NV – March 2025 – The era of...
Level Up Your SOC Skills: A Deep Dive into The SOC Playbook
In today’s world, cyber threats are everywhere — and they’re getting smarter every day. That’s where a Security Operations Center (SOC) comes in. Think of it as the central command room for defending against hackers, malware, and all kinds of digital trouble. If you’re working...
A Practical Guide to Honeypots
In this section, we describe Network Intrusion Detection Systems (IDS)—the traditional approach to network security.We also introduce honeypots, providing a brief history of their development. Finally, we discuss the general advantages and disadvantages of honeypots in modern cybersecurity. 1.1 Network Intrusion Detection System The goal...
Python for Cybersecurity: Practical Applications and Beginner Projects
Python has become one of the most popular programming languages in the world—and it's a favorite among cybersecurity professionals too. But why? Well, Python is easy to learn, super flexible, and comes with tons of libraries that make life easier for ethical hackers, security analysts,...
GitHub Recon: The Underrated Technique to Discover High-Impact Leaks in Bug Bounty
When it comes to bug bounty hunting or red teaming, most folks start with the usual suspects — subdomain enumeration, port scanning, Shodan dorking… the list goes on. But let me let you in on a powerful, underrated gem in the recon game: GitHub Recon....
How to Make a Professional Honeypot to Defend Your Network
In cybersecurity, a honeypot isn’t a jar of honey – it’s a decoy system designed to lure in attackers. It mimics a vulnerable server or service, appearing as a juicy target (like an open SSH or database) while actually being isolated and closely monitored. Any...
The Real Pentesting Starter Pack: No Fluff, Just Labs and Grind
Ready to dive into pentesting? Forget the theory overload – the real learning happens in your own beginner pentesting lab. Think of it as your personal, safe hacking playground on your computer. As one guide bluntly puts it, “nothing beats real, hands-on experience” – so...
Why Every Beginner Pentester Should Build Their Own Lab (Before Getting Certified)
If you're getting started in penetration testing, you might already be eyeing that first certification. But hold on a second – before you even think about getting certified, there’s one crucial step to tackle: build your own pentesting lab. Why? Because nothing beats real, hands-on...
I’ve Interviewed Dozens of Cybersecurity Professionals — Here’s My Best Advice
Hey guys, Rocky here—you probably know me as the founder of CodeLivly. A few weeks ago I got a call I didn’t expect: a Kathmandu-based cybersecurity company asked if I’d consider joining them as a fractional security strategist. (Spoiler: I said “let’s talk.”) While we...
The Pentester Playbook – Get Started To Hacking
When you hear the word “hacking,” you might picture someone in a hoodie typing away in the dark, breaking into banks or stealing data. But here’s the truth: not all hackers are bad — and hacking isn’t just for the movies anymore. In today’s world,...
How to Create a Linux Bash Script – And What You Can Do With It
So, you’ve heard about Bash scripting and you’re curious what all the buzz is about? Whether you're just starting with Linux or diving deeper into automation, Bash scripts are your best friend. They’re like small sets of instructions that you write once, and they do...
Cloud Engineer Roadmap: The Complete Guide from Beginner to Expert (2025 Edition)
If you've been wondering how to become a cloud engineer, you're in the right place. Whether you're just starting out in tech or looking to switch your career, cloud engineering is one of the hottest and fastest-growing fields out there. And the best part? You...
Mastering SQL Injection Recon – Step-by-Step Guide for Bug Bounty Hunters
Picture this: You’re testing a website, and with a simple tweak to a login form—BAM!—you trick the database into spilling its secrets. No password? No problem. That’s the power of SQL Injection (SQLi), one of the most dangerous (and profitable) vulnerabilities in web security. Despite...
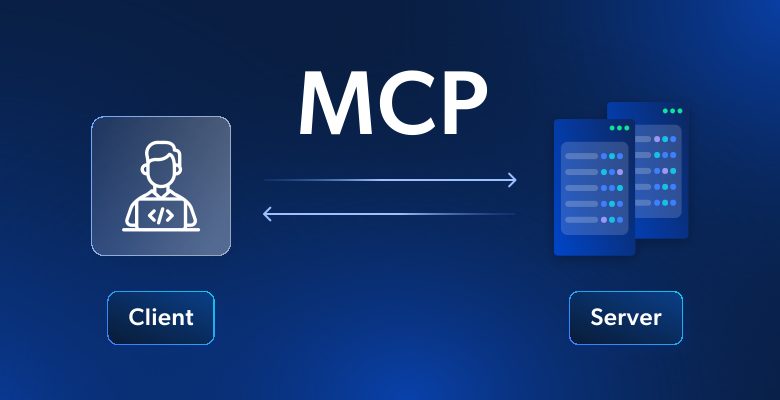
Is it secure to use an MCP server?
The Model Context Protocol (MCP) is a convenient open protocol for linking large-scale language models (LLMs) with external data sources and tools. However, since anyone can create an MCP server and publish it on GitHub, there is a possibility that it may contain malicious code....
Don’t Get Hacked by Jargon! The Cybersecurity Glossary Everyone Needs
Hey there! Welcome to your go-to guide for cyber security terms, abbreviations, and acronyms. Whether you're just starting out in cybersecurity or need a quick refresher, this glossary will help you decode all the techy jargon. Why Does This Stuff Matter? Cyber threats are everywhere,...
Ultimate Guide: Hosting a Live Website in Termux with Nginx & Apache! 🚀
Do you want to turn your Android phone into a fully functional web server? With Termux, you can run Nginx or Apache to host a live website locally—or even make it public! This in-depth guide will walk you through setting up both web servers, configuring...
Now it’s clear! Explaining the basics of IP addresses and their allocation for beginners
Hey guys , I'm Rocky. This may seem sudden, but have you ever thought about what an IP address is?When you use a smartphone or computer, you can connect to the Internet without even thinking about it, and you can watch YouTube or upload photos...
The Ethical Hacker’s Playbook for Hacking Web Servers
So you’re interested in cracking the code of how hackers navigate web servers like they own the place? Well, welcome to the dark side—of knowledge. It’s not a tutorial on rampaging; it’s your backstage pass to hacker thinking so you can outsmart ’em. It’s your...
Analysis of sudo privilege escalation techniques to obtain root through C language under Linux
Sudo privilege escalation is a technique that allows an attacker to gain root access on a Linux system. While sudo is a powerful tool for system administration, it can become a potential security risk if misconfigured or exploited. This article will dive into how attackers...
Mastering Exploit Development: The Key Skill for Professional Cybersecurity Practitioners
Have you read about hackers breaking into gateway systems and stealing proprietary information, or even shutting down entire networks? But how do hackers gain access to it? Much of the answer is exploit development, the art of finding software vulnerabilities and weaponizing those vulnerabilities for...
Exploit Development Made Easy: Generating Payloads In Metasploit
When developing exploits, creating shellcode is a necessary step. Metasploit provides an easy way to generate payloads from within the msfconsole. When you select a specific payload, Metasploit automatically adds useful commands such as "generate", "pry", and "reload". Among these commands, "generate" is the key...
The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of networking tools! Whether you’re a cybersecurity newbie, a network admin, or just a curious techie, this tutorial will turn you into an Nmap ninja by the time we’re done....
Hacking like a Pro: The Ultimate Guide to Penetration Testing with Kali Linux Tools in 2025
Penetration testing is an essential part of any comprehensive security program, and Kali Linux is a powerful platform for conducting such testing. With its vast array of built-in tools and support for third-party software, Kali Linux is a favorite of security professionals and penetration testers...
Search
Recent Posts
AI Hacking Teams Now Autonomously Exploit “Zero-Day” Vulnerabilities, Research Reveals
A groundbreaking new...