In the digital age, access control plays a vital role in safeguarding sensitive information and protecting valuable resources. It forms the foundation of a secure environment, ensuring that only authorized individuals can access specific data, systems, or functionalities. However, the presence of broken access control vulnerabilities can jeopardize this delicate balance, exposing organizations to various risks, including unauthorized access, data breaches, and regulatory non-compliance.
In this article, we delve into the world of broken access control vulnerabilities, exploring their nature, implications, and potential countermeasures. We will discuss common access control models such as DAC, MAC, and RBAC, examining their strengths and weaknesses. Furthermore, we will explore the techniques used to identify and exploit broken access control vulnerabilities, shedding light on the methods employed by malicious actors.
Understanding the dangers associated with broken access control attacks is crucial in devising effective preventive measures. We will explore the reasons why broken access control attacks are particularly dangerous, highlighting the potential consequences that organizations may face when their access control mechanisms are compromised.
Moreover, this article aims to provide comprehensive guidance on mitigating broken access control vulnerabilities. We will delve into best practices for access control, outlining the steps organizations can take to prevent such vulnerabilities from arising in the first place. We will explore techniques for identifying access control vulnerabilities, equipping organizations with the necessary tools and knowledge to assess and strengthen their access control mechanisms.
By embracing a proactive approach to access control, organizations can enhance their security posture and protect their sensitive assets from unauthorized access. Through the adoption of industry best practices, continuous monitoring, and security awareness, organizations can build a robust defense against broken access control vulnerabilities, safeguarding their digital resources and maintaining the trust of their stakeholders.
Join us as we navigate the realm of broken access control vulnerabilities, empowering you with the insights and strategies needed to fortify your organization’s access control framework and ensure the confidentiality, integrity, and availability of your critical assets.
What is Access Control?
Imagine a grand castle with towering walls, safeguarding its precious treasures from prying eyes and unwelcome intruders. At the heart of this fortified stronghold lies a powerful figure known as the Access Control, the keymaster of the castle’s digital domains.
Access Control is the guardian that determines who gets the golden keys to enter the castle, navigate its chambers, and access its valuable secrets. It acts as a gatekeeper, wielding the power to grant or deny passage to individuals seeking entry.
In the realm of digital systems, Access Control takes on a similar role. It is a sophisticated mechanism that safeguards the virtual fortresses we build to protect sensitive information, resources, and functionalities. Like an astute sentry, it enforces rules and regulations, ensuring that only authorized entities are granted access while keeping intruders at bay.
Access Control establishes a hierarchy of permissions, assigning different levels of authority to individuals or groups. It acts as the discerning judge, evaluating credentials, roles, and privileges before granting or denying access to various parts of the digital kingdom.
Just as castle gates swing open for loyal knights and trusted allies, Access Control governs the paths within a system, dictating who can view, modify, or interact with its components. It establishes boundaries, partitions, and limitations, maintaining order and security in the digital realm.
From the humblest personal computers to vast corporate networks, Access Control weaves its intricate tapestry, orchestrating the dance between users and systems. It empowers organizations to strike a delicate balance, granting access to those who need it while keeping potential threats at arm’s length.
So, next time you log into a system, remember the silent sentinel that guards your digital haven, ensuring that only those with the rightful keys can unlock its treasures. Access Control stands as the fortress’s protector, defending against the ever-present dangers that lurk beyond its walls.
What is Broken Access Control?

Access Control is a critical component of any digital system’s security architecture, establishing the boundaries and permissions that dictate who can access which parts of the system. However, when Access Control mechanisms are misconfigured, incomplete, or insufficiently tested, they can become vulnerable to exploitation by malicious actors.
Broken Access Control refers to a class of vulnerabilities that arise when Access Control mechanisms fail to prevent unauthorized access to sensitive data, functions, or resources. Attackers can use these vulnerabilities to gain elevated privileges, manipulate data, or execute unauthorized actions.
Broken Access Control can take many forms, from privilege escalation and vertical access control bypass to horizontal access control bypass and forced browsing. These vulnerabilities can occur at various stages of the Access Control workflow, such as during authentication, authorization, session management, or input validation.
The consequences of Broken Access Control can be severe, leading to data breaches, theft of confidential information, system compromise, or even complete system takeover. Attackers can exploit these vulnerabilities to bypass security measures, escalate their privileges, and gain access to sensitive data or system functionality.
Broken Access Control vulnerabilities are prevalent in many systems, from web applications to mobile devices and cloud-based services. They are often the result of misconfigured or poorly implemented Access Control mechanisms, such as incorrect permission assignments, weak authentication methods, or insufficient validation of user input.
Why are Broken Access Control Attacks Dangerous?

In the vast digital landscape, where virtual fortresses safeguard our most valuable assets, Broken Access Control emerges as a formidable specter, concealing a sinister power that can unleash chaos and wreak havoc upon unsuspecting systems. Let us unveil the dangerous nature of these attacks and the potential calamities they bring forth.
Like a skilled lock-picker armed with forbidden knowledge, attackers who exploit Broken Access Control vulnerabilities can navigate through the system’s defenses unnoticed, slipping through the cracks of the digital realm. With each successful breach, they can commandeer sensitive data, manipulate critical functions, or assume unauthorized roles within the system’s delicate ecosystem.
The repercussions of Broken Access Control attacks reverberate far and wide, permeating every aspect of an organization’s existence. Here’s a glimpse into the perils they pose:
- Cataclysmic Data Breaches: Attackers, armed with illicit access, can seize the crown jewels of sensitive information—customer data, trade secrets, financial records—unleashing the fury of privacy violations, regulatory non-compliance, and irreversible damage to an organization’s reputation.
- Insidious Insider Threats: Broken Access Control opens the gates to malicious insiders, allowing them to exploit their knowledge of the system’s vulnerabilities. These betrayers within the digital castle can manipulate data, disrupt operations, or inflict targeted sabotage, leaving organizations defenseless against their dark intentions.
- Rampant Privilege Escalation: By skillfully navigating the labyrinthine maze of flawed access restrictions, attackers can elevate their privileges, granting themselves godlike powers within the system. With this newfound authority, they can manipulate critical functions, bypass security measures, or sow chaos from within, leaving organizations vulnerable and compromised.
- Erosion of Trust: When access controls crumble, trust in digital systems erodes. Customers, partners, and stakeholders lose confidence, questioning the ability of organizations to protect their assets. This erosion can lead to shattered relationships, disrupted business operations, and severe financial ramifications.
- Regulatory Consequences: In the realm of compliance, Broken Access Control stands as a glaring violation. Regulatory bodies and industry standards demand robust access management to protect sensitive data and ensure the integrity of systems. Failure to address these vulnerabilities can result in hefty penalties, legal ramifications, and a loss of market standing.
The dangers of Broken Access Control attacks serve as a sobering reminder of the relentless vigilance required to protect our digital domains. Organizations must fortify their defenses, diligently assess and mitigate vulnerabilities, and instill a culture of security to ward off the malevolent forces that seek to exploit the cracks in our digital armor.
For in the realm of technology, where the interconnectedness of our world grows ever deeper, the consequences of Broken Access Control attacks can be likened to a wildfire, rapidly spreading through the digital landscape, leaving a path of destruction in its wake. Only through proactive defense and unwavering commitment can we safeguard our kingdoms from this formidable menace.
Access Control Attack Scenarios
Scenario 1: A banking application has horizontal permission issues. Imagine this simple scenario where an attacker logs into a banking application using their own account details. When the attacker views their account, the browser makes a request to the webserver for the account numbers balance and recent transactions.
An attacker observes the following request made by the application when loading their banking dashboard.
- https://mybankingapp.test/cgi-bin/hpe.py?accountId=4462
The attacker modifies the request to use the bank account number of another user by changing the accountID parameter from 4462 to 4463.
- https://mybankingapp.test/cgi-bin/hpe.py?accountId=4463
The application’s response provides the attacker with another person’s account details.
- {“AccountID”: 4463, “Balance”: “$167,183.09”}
Scenario 2: A banking application has vertical permission issues. Building on the previous example, the banking application has a customer support role that allows customer support agents to help customers with account issues. The customer support role has the ability to search a database of all customers which is not available to customers. The attacker discovers that this feature exists through some comments left in the web page’s source code.
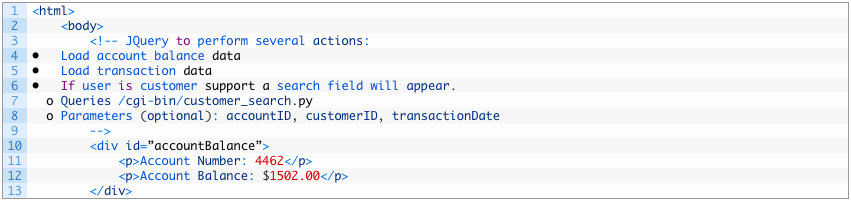
The attacker crafts a request based on this information to search the customer database.
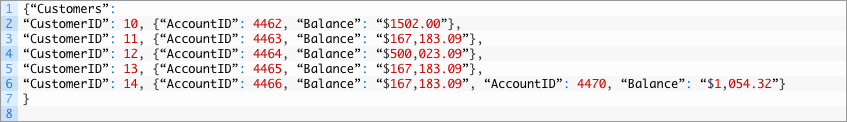
- https://mybankingapp.test/cgi-bin/customer_search.py?limit=5
The application responds with a list of 100 customers from the application’s database.
In addition to manipulating request parameters and URL paths, exploitation commonly involves tampering of metadata such as session tokens, cookies, or CORS misconfigurations.
Understanding Access Control Mechanisms
Types of Access Control Mechanisms
Access Control mechanisms serve as the guardians of our digital domains, regulating the flow of information and determining who gains entry to sensitive resources. To fulfill this crucial role, various types of Access Control mechanisms have been developed, each with its unique approach to securing the virtual gates. Let’s explore the prominent types:
- Discretionary Access Control (DAC): In the realm of Discretionary Access Control, power lies in the hands of the resource owner. Here, the owner possesses the authority to define access permissions and determine who can access their resources. Access decisions are discretionary, allowing for flexibility but potentially introducing inconsistencies if owners are not vigilant in their access management.
- Mandatory Access Control (MAC): Mandatory Access Control places the responsibility of access decisions in the hands of the system administrators or security administrators. Access is granted based on predefined security labels or clearances assigned to users and resources. This mechanism ensures strict control over sensitive data and enforces consistent security policies throughout the system.
- Role-Based Access Control (RBAC): Role-Based Access Control grants access based on user roles and their associated permissions. Users are assigned specific roles within an organization, and access is granted based on those roles rather than individual identities. RBAC simplifies access management, improves scalability, and ensures a level of consistency in permissions across users with similar responsibilities.
- Attribute-Based Access Control (ABAC): Attribute-Based Access Control takes a granular approach to access decisions, considering various attributes associated with users, resources, and environmental factors. Policies are defined using attributes such as user attributes (e.g., job title, department), resource attributes (e.g., sensitivity, classification), and environmental attributes (e.g., time of access, location). ABAC allows for flexible and fine-grained access control but requires a robust infrastructure for attribute evaluation.
- Rule-Based Access Control (RBAC): Rule-Based Access Control employs a set of rules that govern access decisions. Access requests are evaluated against predefined rules, and permissions are granted or denied accordingly. Rules can be based on various factors, including user identity, time of access, resource attributes, and contextual information. RBAC offers flexibility in defining complex access policies but can be challenging to manage at scale.
- Hierarchical Attribute-Based Access Control (HABAC): Hierarchical Attribute-Based Access Control extends ABAC by introducing hierarchical relationships among attributes. It allows for the definition of complex access policies based on multiple levels of attributes, creating a hierarchical structure. HABAC provides a flexible and scalable approach to access control, particularly suitable for complex organizational structures.
Each type of Access Control mechanism presents its own strengths and weaknesses, addressing different security requirements and organizational needs. Understanding these mechanisms enables organizations to select the most appropriate approach to protect their digital assets, fortifying their defenses against unauthorized access and safeguarding the sanctity of their virtual realms.
Common Access Control Models (DAC, MAC, RBAC)
In the realm of information security, several Access Control models have been developed to provide structure and enforce order within digital systems. These models serve as frameworks for implementing access management policies and determining who can access what resources. Let’s explore the three common Access Control models:
- Discretionary Access Control (DAC): Discretionary Access Control is a widely used Access Control model that allows resource owners to have discretion over access decisions. In DAC, owners have the authority to define access permissions and determine who can access their resources. Access is granted based on the identity or group membership of the requester. While DAC provides flexibility and allows for collaboration, it can lead to inconsistencies if owners are not vigilant in their access management.
- Mandatory Access Control (MAC): Mandatory Access Control takes a more stringent approach to access management by assigning security labels or clearances to both users and resources. Access decisions are made by system administrators or security administrators based on these labels. MAC ensures a hierarchical and consistent enforcement of access policies throughout the system. This model is commonly employed in environments with strict security requirements, such as government or military systems.
- Role-Based Access Control (RBAC): Role-Based Access Control is a popular model that grants access based on predefined roles assigned to users. Users are assigned specific roles within an organization, reflecting their responsibilities and job functions. Access permissions are associated with roles rather than individual identities. RBAC simplifies access management by grouping users with similar access needs and ensures a level of consistency in permissions across those roles. This model is scalable, efficient, and widely adopted in various industries.
Each Access Control model offers different advantages and is suited for specific use cases. DAC emphasizes flexibility and owner control, MAC emphasizes strict hierarchical control, and RBAC emphasizes efficient role-based management. Organizations often adopt a combination of these models or select the one that best aligns with their security requirements and operational needs.
By implementing these Access Control models, organizations can establish a robust framework for managing access, safeguarding sensitive data, and maintaining the integrity and confidentiality of their digital realms.
Strengths and Weaknesses of Access Control Mechanisms
Access Control mechanisms serve as the cornerstone of secure access management, providing a vital layer of protection for digital systems and sensitive resources. However, like any security measure, these mechanisms have their strengths and weaknesses. Understanding these aspects is crucial for implementing effective access control strategies. Let’s examine the strengths and weaknesses of Access Control mechanisms:
- Discretionary Access Control (DAC):
Strengths:
- Flexibility: DAC offers resource owners the flexibility to define access permissions based on their discretion.
- Collaboration: DAC facilitates collaboration by allowing resource owners to share access with other users.
- Simplicity: DAC is relatively easy to understand and implement, making it widely adopted in various systems.
Weaknesses:
- Inconsistent enforcement: Since access decisions are left to the resource owners’ discretion, inconsistencies can arise in access control policies.
- Over-privilege risks: Resource owners may grant excessive permissions, increasing the risk of unauthorized access or data breaches.
- Limited scalability: As the number of users and resources increases, managing access control lists (ACLs) in DAC can become challenging.
- Mandatory Access Control (MAC):
Strengths:
- Strong enforcement: MAC enforces access control based on predefined security labels or clearances, ensuring consistent and strict access policies.
- Centralized control: Administrators have centralized control over access decisions, reducing the risk of inconsistent access control settings.
- Defense against insider threats: MAC helps mitigate insider threats by restricting access based on predefined security classifications.
Weaknesses:
- Complexity: Implementing and managing MAC can be complex, requiring significant planning and coordination.
- Lack of flexibility: MAC’s strict enforcement may limit the flexibility needed in dynamic environments or collaborative workflows.
- Administrative overhead: Frequent updates to security labels and clearances can introduce administrative overhead and complexity.
- Role-Based Access Control (RBAC):
Strengths:
- Scalability: RBAC simplifies access management by grouping users into roles, reducing the complexity of access control administration.
- Efficient permission assignment: RBAC allows for efficient assignment of permissions based on predefined roles, minimizing the risk of over-privilege.
- Compliance and auditing: RBAC aids in compliance efforts by providing a clear audit trail of user roles and their associated permissions.
Weaknesses:
- Role explosion: Without proper role design and maintenance, RBAC can lead to role proliferation, making administration and updates challenging.
- Limited granularity: RBAC may not provide fine-grained control needed in certain scenarios where access control requires more attributes than roles alone.
- Complex role engineering: Designing and maintaining a well-defined RBAC system requires careful planning, role definition, and ongoing management.
It is important to note that the strengths and weaknesses of Access Control mechanisms should be considered in the context of specific system requirements, compliance regulations, and the overall security posture of the organization. A combination of these mechanisms or the adoption of hybrid models can often mitigate the weaknesses while leveraging the strengths to achieve a robust and effective access management strategy.
Identifying Broken Access Control Vulnerabilities

Broken Access Control vulnerabilities pose a significant threat to the security of digital systems, making it crucial to proactively identify and address them. Detecting these vulnerabilities requires a comprehensive approach that combines careful analysis, testing, and assessment. Here’s a brief overview of the methods commonly used to identify Broken Access Control vulnerabilities:
How to Identify Access Control Vulnerabilities
Ensuring the integrity and effectiveness of access control mechanisms is paramount in maintaining a secure digital environment. To identify potential access control vulnerabilities, organizations should employ a systematic and professional approach. Here are key steps to follow when identifying access control vulnerabilities:
- Conduct a Thorough Access Control Policy Analysis: Begin by reviewing the access control policies and guidelines implemented within the system. This involves examining the documentation, configuration files, and access control matrices to understand how permissions are granted, managed, and enforced.
- Perform Access Control Configuration Review: Analyze the configuration settings of access control mechanisms, such as user roles, permissions, and group memberships. Evaluate whether the configurations align with security best practices and business requirements. Look for misconfigurations, inconsistencies, or gaps that may expose vulnerabilities.
- Employ Security Testing Techniques: Utilize various security testing techniques to identify potential vulnerabilities. These may include:a. Authentication Testing: Verify the strength and effectiveness of authentication mechanisms, such as password policies, multi-factor authentication, or session management controls. Test for weaknesses like weak passwords, session fixation, or session hijacking.b. Authorization Testing: Assess the accuracy and robustness of authorization mechanisms. Test for scenarios where users can escalate privileges, access unauthorized resources, or manipulate permissions. Consider both horizontal and vertical privilege escalation.c. Input Validation Testing: Validate the input validation mechanisms to ensure they properly handle user-supplied data. Test for injection attacks, such as SQL injection or cross-site scripting (XSS), which can bypass access controls.
- Conduct User and Role Mapping Analysis: Review user accounts, roles, and their associated permissions. Identify any inconsistencies, excessive privileges, or orphaned accounts that may result in unauthorized access. Analyze the assignment and revocation processes of user roles.
- Perform Security Code Reviews: Examine the source code and application logic for access control vulnerabilities. Look for issues like direct object references, insecure direct object manipulation, or lack of proper input validation that can lead to unauthorized access.
- Utilize Vulnerability Scanners and Automated Tools: Employ automated vulnerability scanning tools specifically designed to detect access control weaknesses. These tools analyze the system’s configuration, behavior, and access patterns to identify potential vulnerabilities, misconfigurations, or access control bypasses.
- Regularly Conduct Security Audits: Perform regular security audits to evaluate the overall effectiveness of access control mechanisms. This includes reviewing access logs, monitoring access patterns, and conducting compliance checks against industry standards and regulatory requirements.
By following these professional steps, organizations can identify access control vulnerabilities and take necessary remedial actions. It is crucial to establish a proactive security culture, conduct regular assessments, and implement strong access control practices to mitigate the risks associated with unauthorized access and maintain a robust security posture.
Common Types of Access Control Vulnerabilities
Access control vulnerabilities can expose digital systems to unauthorized access, data breaches, and compromise the confidentiality, integrity, and availability of sensitive resources. Understanding the common types of access control vulnerabilities is crucial for effectively mitigating risks and enhancing the security of an organization’s digital assets. Here are some of the most prevalent access control vulnerabilities:
- Privilege Escalation: Privilege escalation vulnerabilities occur when an attacker gains higher privileges or access rights than intended. This can be achieved through exploiting flaws in user authentication mechanisms, bypassing authorization checks, or leveraging misconfigurations in access control settings. Privilege escalation can lead to unauthorized access to sensitive data or the ability to modify critical system configurations.
- Insecure Direct Object References (IDOR): IDOR vulnerabilities arise when access controls fail to properly validate and enforce restrictions on direct object references, such as URLs or database keys. Attackers can manipulate these references to access unauthorized resources or perform actions that should be restricted. IDOR vulnerabilities commonly occur when direct object references are predictable or insufficiently validated.
- Access Control Bypass: Access control bypass vulnerabilities occur when an attacker finds a way to circumvent access controls altogether, granting unauthorized access to resources. This can be achieved through flaws in authentication mechanisms, bypassing client-side controls, exploiting business logic errors, or leveraging insecure direct object references. Access control bypass can result in the exposure of sensitive data, unauthorized operations, or privilege escalation.
- Insufficient or Weak Password Policies: Weak password policies, such as allowing easily guessable passwords or neglecting to enforce password complexity requirements, can lead to access control vulnerabilities. Attackers can exploit weak passwords to gain unauthorized access to user accounts or administrative privileges. Additionally, inadequate password storage mechanisms, such as storing passwords in plain text or using weak encryption, can expose passwords to unauthorized disclosure.
- Inadequate Session Management: Flaws in session management mechanisms can result in access control vulnerabilities. Examples include session fixation, where an attacker fixes or hijacks a valid user’s session, or session timeout issues, where sessions remain active for extended periods even after a user has logged out. Inadequate session management can lead to unauthorized access, session hijacking, or session-related attacks.
- Misconfigured Access Control Settings: Misconfigurations in access control settings, such as incorrect permission assignments, improper role-based access controls, or over-privileged accounts, can introduce vulnerabilities. These misconfigurations can grant excessive privileges, allowing unauthorized access to sensitive resources or compromising the principle of least privilege.
- Lack of Granularity in Access Controls: Insufficient granularity in access controls can result in vulnerabilities. When access controls are too broad or lack fine-grained restrictions, it becomes challenging to enforce precise permissions, potentially leading to unauthorized access or privilege escalation. Lack of granularity may occur when access control policies are not aligned with the sensitivity levels of the resources.
To mitigate these vulnerabilities, organizations should adopt a defense-in-depth approach. This includes implementing secure coding practices, conducting regular security assessments, employing robust authentication and authorization mechanisms, enforcing strong password policies, implementing secure session management, and continuously monitoring and auditing access controls. By addressing these vulnerabilities, organizations can bolster their access control systems and reduce the risk of unauthorized access and data breaches.
Tools and Techniques for Identifying Broken Access Control Vulnerabilities
Identifying broken access control vulnerabilities is a critical step in securing digital systems and preventing unauthorized access. Here are some tools and techniques that can help identify access control vulnerabilities:
- Manual Code Review: A manual code review involves analyzing the application’s source code to identify potential access control vulnerabilities. Reviewers look for coding errors that could lead to privilege escalation, insecure direct object references, or other access control bypass techniques. This method requires a skilled reviewer with knowledge of access control mechanisms and is time-consuming but provides a comprehensive analysis of the system.
- Automated Scanning Tools: Automated scanning tools, such as Burp Suite, can help identify access control vulnerabilities in web applications. These tools scan the application for vulnerabilities, including access control flaws, and provide a report of identified issues. Automated scanning tools can help identify vulnerabilities faster and provide an initial assessment of the system’s security posture.
- Penetration Testing: Penetration testing involves simulating a real-world attack against the system to identify potential access control vulnerabilities. Penetration testers attempt to bypass access controls and escalate privileges to gain unauthorized access to resources. This technique requires skilled testers with knowledge of access control mechanisms and is a comprehensive way to test the system’s security.
- Threat Modeling: Threat modeling involves identifying potential threats to the system and evaluating the system’s security controls to address those threats. Access control vulnerabilities can be identified through this process by assessing the system’s access control mechanisms against potential threats. Threat modeling is an effective technique for identifying vulnerabilities early in the development process and implementing security controls to address them.
- Fuzz Testing: Fuzz testing involves sending large amounts of input data to the system to identify vulnerabilities. Access control vulnerabilities can be identified through this process by sending input data that violates access control policies, such as attempting to access unauthorized resources. Fuzz testing is an effective technique for identifying vulnerabilities that may not be identified through other methods.
In conclusion, identifying broken access control vulnerabilities requires a comprehensive approach that involves a combination of manual and automated techniques. Organizations should adopt a defense-in-depth approach, including secure coding practices, regular security assessments, and continuous monitoring and auditing of access controls, to identify and address access control vulnerabilities.
Mitigating Broken Access Control Attacks

Mitigating broken access control vulnerabilities is crucial to maintaining a secure digital environment. By implementing best practices for access control and employing preventive techniques, organizations can significantly reduce the risk of unauthorized access and data breaches. Here are some recommended practices and techniques for mitigating broken access control vulnerabilities:
Best Practices for Access Control
- Principle of Least Privilege (PoLP): Grant users the minimum privileges necessary to perform their tasks. Avoid assigning excessive permissions or broad access rights that could increase the attack surface.
- Role-Based Access Control (RBAC): Implement RBAC to manage access control in a structured manner. Assign permissions to roles and then assign roles to users. This simplifies access management and ensures consistency.
- Strong Authentication: Enforce strong authentication mechanisms, such as multi-factor authentication (MFA) or biometrics, to verify user identities and protect against unauthorized access.
- Regular Access Reviews: Conduct regular reviews of user access rights and permissions to ensure they align with business needs. Remove or modify unnecessary privileges for users who no longer require them.
- Secure Password Policies: Enforce strong password policies, including minimum length, complexity requirements, and regular password updates. Educate users about the importance of creating strong passwords and avoiding common pitfalls.
- Secure Session Management: Implement secure session management practices, including session timeouts, secure cookie handling, and protection against session hijacking or fixation attacks.
- Error Handling: Implement proper error handling mechanisms to avoid revealing sensitive information that could aid attackers in exploiting access control vulnerabilities.
- Regular Monitoring and Auditing: Implement robust logging and monitoring mechanisms to detect suspicious activities, access patterns, and potential access control breaches. Regularly review access logs and audit trails for any anomalies or unauthorized access attempts.
- Security Awareness and Training: Educate users, developers, and administrators about access control best practices, common attack vectors, and the importance of security awareness. Promote a culture of security consciousness throughout the organization.
- Secure Development Practices: Follow secure coding practices and conduct thorough security testing during the development phase to identify and address access control vulnerabilities early in the software development lifecycle.
How to Prevent Broken Access Control Vulnerabilities
- Design Access Controls with Security in Mind: Implement a secure and well-designed access control model from the beginning of the system development process. Consider factors such as user roles, permissions, and resource hierarchies to ensure proper enforcement of access control policies.
- Use Standardized Frameworks and Libraries: Leverage established access control frameworks and libraries that have undergone rigorous security testing and have a proven track record of reliability. Avoid reinventing access control mechanisms, as this increases the likelihood of introducing vulnerabilities.
- Validate and Sanitize User Input: Implement robust input validation and data sanitization techniques to prevent access control vulnerabilities arising from malicious user input. Validate and sanitize all user-supplied data to mitigate the risk of injection attacks, such as SQL injection or cross-site scripting (XSS).
- Implement Fine-Grained Access Controls: Employ granular access controls to ensure that users are granted only the necessary permissions required to perform their specific tasks. Avoid using overly broad access rules, as this can increase the attack surface and lead to unauthorized access.
- Enforce Secure Session Management: Implement secure session management practices, such as session timeouts, secure cookie handling, and protection against session fixation attacks. Invalidate sessions upon user logout and regularly rotate session tokens to mitigate the risk of session-related vulnerabilities.
- Perform Regular Security Testing: Conduct comprehensive security assessments, including penetration testing and vulnerability scanning, to identify and address access control vulnerabilities. Regularly test access control mechanisms to verify their effectiveness under different scenarios and simulate potential attack vectors.
- Apply Secure Coding Practices: Follow secure coding guidelines and best practices to minimize the introduction of access control vulnerabilities during the development phase. Use secure coding techniques, such as input validation, output encoding, and proper error handling, to mitigate common security risks.
- Continuously Monitor and Audit Access Controls: Implement robust logging and monitoring mechanisms to detect suspicious activities, access patterns, and potential access control breaches. Regularly review access logs and audit trails to identify any anomalies or unauthorized access attempts.
- Provide Security Awareness Training: Educate users, developers, and administrators about the importance of access control, common vulnerabilities, and best practices. Promote a culture of security awareness and encourage reporting of potential access control issues or suspicious activities.
- Stay Updated with Security Patches and Updates: Keep software, systems, and access control components up to date with the latest security patches and updates. Stay informed about security advisories and promptly address any identified vulnerabilities to mitigate risks.
By following these preventive measures, organizations can significantly reduce the likelihood of broken access control vulnerabilities and enhance the overall security posture of their systems. It is important to implement a proactive approach, regularly assess security controls, and adapt to evolving threats to maintain effective access control measures.
Techniques for Mitigating Broken Access Control Vulnerabilities
- Access Control Testing: Conduct thorough testing of access control mechanisms to identify vulnerabilities and weaknesses. This includes testing for privilege escalation, insecure direct object references, access control bypass, and other common attack vectors specific to the system being assessed.
- Secure Configuration Management: Ensure that access control configurations are securely managed and regularly reviewed. Implement a robust change management process to monitor and control changes to access control settings, minimizing the risk of misconfigurations that could lead to vulnerabilities.
- Secure Session Management: Implement secure session management practices, such as using secure session tokens, enforcing session timeouts, and protecting session data from tampering or disclosure. Verify that sessions are properly invalidated upon user logout and that session tokens are adequately protected to prevent session-related attacks.
- Role-Based Access Control (RBAC): Adopt RBAC principles to organize access control policies and permissions. Assign permissions based on predefined roles rather than directly to individual users. Regularly review and update role assignments to ensure they reflect the current requirements and responsibilities of users.
- Attribute-Based Access Control (ABAC): Consider implementing ABAC, which grants access based on a combination of attributes such as user attributes, environmental factors, and resource attributes. ABAC provides more fine-grained control and flexibility in defining access control policies.
- Secure Authentication Mechanisms: Utilize strong and secure authentication methods, such as multi-factor authentication (MFA) or biometrics, to enhance the security of access control. Ensure that authentication mechanisms are properly implemented, including password hashing, secure storage of credentials, and protection against brute-force attacks.
- Continuous Monitoring and Auditing: Implement robust logging and monitoring systems to track access control activities, detect anomalies, and identify potential access control breaches. Regularly review and analyze access logs to identify suspicious behavior or unauthorized access attempts.
- Regular Access Reviews: Conduct regular reviews of user access rights and permissions to ensure they align with business needs and adhere to the principle of least privilege. Remove or modify unnecessary privileges for users who no longer require them.
- Secure Development Practices: Implement secure coding practices throughout the software development lifecycle to prevent the introduction of access control vulnerabilities. Conduct code reviews, utilize static code analysis tools, and educate developers on secure coding techniques.
- Security Awareness and Training: Provide comprehensive security awareness training to users, developers, and administrators to educate them about access control best practices, common vulnerabilities, and the importance of adhering to security policies and procedures.
By employing these techniques, organizations can mitigate broken access control vulnerabilities and enhance the overall security of their systems. It is essential to implement a proactive and holistic approach, integrating security into all stages of system development and maintenance. Regular assessments, updates, and user education are vital components of a robust access control strategy.
Conclusion
In conclusion, access control is a crucial aspect of information security that regulates access to resources and data within an organization. Broken access control vulnerabilities can pose significant risks to organizations, leading to data breaches, system compromises, and reputational damage.
To mitigate these risks, organizations must adopt robust access control mechanisms, including RBAC, ABAC, secure authentication, secure session management, and secure configuration management. Regular testing, auditing, and user education are also critical components of an effective access control strategy.
By implementing best practices for access control and adopting a proactive and holistic approach to security, organizations can minimize the risk of broken access control vulnerabilities and enhance the overall security of their systems. As the threat landscape continues to evolve, it is essential to remain vigilant and proactive in identifying and addressing access control vulnerabilities to protect the integrity and confidentiality of sensitive data.`













